ご注意下さい
この記事は3年以上前に書かれた記事ですので、内容が古い可能性があります。
お知らせ
- 設定に関して過不足や勘違い等の不備がありますので適宜見直しをかけています。
(2021/2/8)以下の修正を行いました
- ClamAVに関してパターンファイルのアップデート方法について追記
- SpamAssassinに関してアップデート方法についての追記
永らく愛用してきたqmailですが、CentOS8化に伴いIPv6に対応しようとしたところIPv6対応が難しかったため、Qmail+Courier-Imapとは訣別し、Postfix+Dovecotで新たに構築しようと思います。またF-Protも残念ながら2021年7月末を以て個人用とのサポートは打ち切られるようです。これを機にアンチウィルスソフトはClamAVに変更しようと思います。
なお、Sophos Antivirus for Linuxについてもサポートが終了した模様です。
この記事のもくじ
構築したいメール環境
さて、構築方法を解説する前に今回私が構築しようとしている環境について説明します。
簡単に解説しますと、私の自宅環境では外部メールサーバーと内部メールサーバーの2台構成です。
メール受信時は、外部メールサーバーはSMTP(25/tcp)を受け付けて、コンテンツチェッカーであるamavisd-newに渡します(tcp/10024)。amavisd-newはウィルスチェックソフトであるClamAVとSpamAssassinを呼び出してメールのチェックをします。
問題が無ければ、Virtualファイルに従いローカル配送かリレー配送します。リレーの場合はtransportファイルでリレールートが決定されます。上記に加えて、iphoneから外部接続しますので、SMTPS(465/tcp)とIMAPS(993/tcp)の口を用意しておく必要があります。また、Postfix + pypolicyd-spfでSPFのチェックもメール受信時に実行していますが、図には表していません。
メール送信時には(図がありませんが)、opendkimにてDKIM署名をして送信、という流れになります。
さて、では設定について見ていきましょう。PostfixとDovecotはインストール済みであるとしています。
Amavisd-New
インストール
Amavisd-newをインストールします。
# dnf install amavisd-new メタデータの期限切れの最終確認: 0:26:55 時間前の 2021年02月03日 19時37分45秒 に実施しました。 エラー: 問題: conflicting requests - nothing provides perl(IO::Stringy) needed by amavis-2.12.1-5.el8.noarch (インストール不可のパッケージをスキップするには、'--skip-broken' を追加してみてください または、'--nobest' を追加して、最適候補のパッケージのみを使用しないでください) #
なんだかperl(IO::stringy)の依存関係チェックでエラーとなりますのでPowertoolsレポジトリを有効にします。
/etc/yum.repos.d/CentOS-Linux-PowerTools.repoを編集して、レポジトリを有効にしましょう。
[powertools]
name=CentOS Linux $releasever - PowerTools
mirrorlist=http://mirrorlist.centos.org/?release=$releasever&arch=$basearch&repo=PowerTools&infra=$infra
#baseurl=http://mirror.centos.org/$contentdir/$releasever/PowerTools/$basearch/os/
gpgcheck=1
enabled=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-centosofficial
# dnf install amavisd-new CentOS Linux 8 - PowerTools 1.5 MB/s | 2.0 MB 00:01 依存関係が解決しました。 ========================================================================================================================================================================================= パッケージ アーキテクチャー バージョン リポジトリー サイズ ========================================================================================================================================================================================= インストール: amavis noarch 2.12.1-5.el8 epel 413 k 依存関係のインストール: altermime x86_64 0.3.10-21.el8 epel 66 k clamav-data noarch 0.103.0-1.el8 epel 220 M clamav-filesystem noarch 0.103.0-1.el8 epel 43 k clamav-lib x86_64 0.103.0-1.el8 epel 853 k libidn x86_64 1.34-5.el8 appstream 239 k libprelude x86_64 5.2.0-1.el8 epel 326 k perl-Archive-Zip noarch 1.60-3.el8 appstream 108 k perl-Authen-SASL noarch 2.16-13.el8 appstream 57 k perl-BerkeleyDB x86_64 0.63-2.el8 epel 154 k perl-Convert-ASN1 noarch 0.27-17.el8 appstream 60 k perl-Convert-BinHex noarch 1.125-13.el8 epel 49 k perl-File-LibMagic x86_64 1.16-9.el8 epel 44 k perl-GSSAPI x86_64 0.28-23.el8 appstream 63 k perl-IO-Multiplex noarch 1.16-9.el8 appstream 31 k perl-IO-stringy noarch 2.111-9.el8 powertools 71 k perl-JSON noarch 2.97.001-2.el8 appstream 96 k perl-MIME-tools noarch 5.509-9.el8 epel 249 k perl-Net-LibIDN x86_64 0.12-35.el8 epel 34 k perl-Net-Server noarch 2.009-3.el8 appstream 209 k perl-Razor-Agent x86_64 2.85-33.el8 epel 123 k perl-Text-Soundex x86_64 3.05-8.el8 appstream 32 k perl-Text-Unidecode noarch 1.30-5.el8 appstream 149 k perl-Unix-Syslog x86_64 1.1-29.el8 appstream 35 k perl-common-sense x86_64 3.7.4-8.el8 powertools 35 k 弱い依存関係のインストール: arj x86_64 3.10.22-30.el8 epel 184 k clamd x86_64 0.103.0-1.el8 epel 121 k freeze x86_64 2.5.0-26.el8 epel 38 k lzop x86_64 1.03-20.el8 baseos 62 k nomarch x86_64 1.4-21.el8 epel 26 k p7zip x86_64 16.02-16.el8 epel 691 k p7zip-plugins x86_64 16.02-16.el8 epel 1.1 M perl-Convert-TNEF noarch 0.18-17.el8 epel 26 k perl-Convert-UUlib x86_64 3:1.8-1.el8 epel 243 k perl-LDAP noarch 1:0.66-7.el8 appstream 386 k unzoo x86_64 4.4-27.el8 epel 30 k トランザクションの概要 ========================================================================================================================================================================================= インストール 36 パッケージ ダウンロードサイズの合計: 227 M インストール済みのサイズ: 239 M これでよろしいですか? [y/N]: 〜〜
設定
Amavisd-New
/etc/amavisd/amavisd.confを編集します。
use strict;
# a minimalistic configuration file for amavisd-new with all necessary settings
#
# see amavisd.conf-default for a list of all variables with their defaults;
# for more details see documentation in INSTALL, README_FILES/*
# and at http://www.ijs.si/software/amavisd/amavisd-new-docs.html
# COMMONLY ADJUSTED SETTINGS:
#@bypass_virus_checks_maps = (1); # controls running of anti-virus code
#@bypass_spam_checks_maps = (1); # controls running of anti-spam code
# $bypass_decode_parts = 1; # controls running of decoders&dearchivers
# $myprogram_name = $0; # set to 'amavisd' or similar to avoid process name
# truncation in /proc/<pid>/stat and ps -e output
$max_servers = 2; # num of pre-forked children (2..30 is common), -m
$daemon_user = 'amavis'; # (no default; customary: vscan or amavis), -u
$daemon_group = 'amavis'; # (no default; customary: vscan or amavis), -g
$mydomain = 'kamata-net.com'; # a convenient default for other settings
$MYHOME = '/var/spool/amavisd'; # a convenient default for other settings, -H
$TEMPBASE = "$MYHOME/tmp"; # working directory, needs to exist, -T
$ENV{TMPDIR} = $TEMPBASE; # environment variable TMPDIR, used by SA, etc.
$QUARANTINEDIR = undef; # -Q
# $quarantine_subdir_levels = 1; # add level of subdirs to disperse quarantine
# $release_format = 'resend'; # 'attach', 'plain', 'resend'
# $report_format = 'arf'; # 'attach', 'plain', 'resend', 'arf'
# $daemon_chroot_dir = $MYHOME; # chroot directory or undef, -R
$db_home = "$MYHOME/db"; # dir for bdb nanny/cache/snmp databases, -D
# $helpers_home = "$MYHOME/var"; # working directory for SpamAssassin, -S
$lock_file = "/run/amavisd/amavisd.lock"; # -L
$pid_file = "/run/amavisd/amavisd.pid"; # -P
#NOTE: create directories $MYHOME/tmp, $MYHOME/var, $MYHOME/db manually
$log_level = 0; # verbosity 0..5, -d
$log_recip_templ = undef; # disable by-recipient level-0 log entries
$do_syslog = 1; # log via syslogd (preferred)
$syslog_facility = 'mail'; # Syslog facility as a string
# e.g.: mail, daemon, user, local0, ... local7
$enable_db = 1; # enable use of BerkeleyDB/libdb (SNMP and nanny)
# $enable_zmq = 1; # enable use of ZeroMQ (SNMP and nanny)
$nanny_details_level = 2; # nanny verbosity: 1: traditional, 2: detailed
$enable_dkim_verification = 1; # enable DKIM signatures verification
$enable_dkim_signing = 1; # load DKIM signing code, keys defined by dkim_key
#@local_domains_maps = ( [".$mydomain","kamata-net.com","kamata-net.jp"] ); # list of all local domains
@local_domains_maps = (1);
@mynetworks = qw( 127.0.0.0/8 [::1] [FE80::]/10 [FEC0::]/10 [2405:6580:27e0:1300::]/64
10.0.0.0/8 172.16.0.0/12 192.168.10.0/24 192.168.30.0/24 );
$unix_socketname = "/run/amavisd/amavisd.sock"; # amavisd-release or amavis-milter
# option(s) -p overrides $inet_socket_port and $unix_socketname
# The default receiving port in the Fedora and RHEL SELinux policy is 10024.
# To allow additional ports you need to label them as 'amavisd_recv_port_t'
# For example: semanage port -a -t amavisd_recv_port_t -p tcp 10022
$inet_socket_port = 10024; # listen on this local TCP port(s)
# $inet_socket_port = [10022,10024]; # listen on multiple TCP ports
$policy_bank{'MYNETS'} = { # mail originating from @mynetworks
originating => 1, # is true in MYNETS by default, but let's make it explicit
os_fingerprint_method => undef, # don't query p0f for internal clients
};
# it is up to MTA to re-route mail from authenticated roaming users or
# from internal hosts to a dedicated TCP port (such as 10022) for filtering
$interface_policy{'10022'} = 'ORIGINATING';
$policy_bank{'ORIGINATING'} = { # mail supposedly originating from our users
originating => 1, # declare that mail was submitted by our smtp client
allow_disclaimers => 1, # enables disclaimer insertion if available
# notify administrator of locally originating malware
virus_admin_maps => ["virusalert\@$mydomain"],
spam_admin_maps => ["virusalert\@$mydomain"],
warnbadhsender => 1,
# forward to a smtpd service providing DKIM signing service
forward_method => 'smtp:[127.0.0.1]:10025',
# force MTA conversion to 7-bit (e.g. before DKIM signing)
smtpd_discard_ehlo_keywords => ['8BITMIME'],
bypass_banned_checks_maps => [1], # allow sending any file names and types
terminate_dsn_on_notify_success => 0, # don't remove NOTIFY=SUCCESS option
};
$interface_policy{'SOCK'} = 'AM.PDP-SOCK'; # only applies with $unix_socketname
# Use with amavis-release over a socket or with Petr Rehor's amavis-milter.c
# (with amavis-milter.c from this package or old amavis.c client use 'AM.CL'):
$policy_bank{'AM.PDP-SOCK'} = {
protocol => 'AM.PDP',
auth_required_release => 0, # do not require secret_id for amavisd-release
};
#$sa_tag_level_deflt = 2.0; # add spam info headers if at, or above that level
$sa_tag_level_deflt = -999; # add spam info headers if at, or above that level
$sa_tag2_level_deflt = 6.2; # add 'spam detected' headers at that level
$sa_kill_level_deflt = 6.9; # triggers spam evasive actions (e.g. blocks mail)
$sa_dsn_cutoff_level = 10; # spam level beyond which a DSN is suppressed
$sa_crediblefrom_dsn_cutoff_level = 18; # likewise, but for a likely valid From
# $sa_quarantine_cutoff_level = 25; # spam level beyond which quarantine is off
$penpals_bonus_score = 8; # (no effect without a @storage_sql_dsn database)
$penpals_threshold_high = $sa_kill_level_deflt; # don't waste time on hi spam
$bounce_killer_score = 100; # spam score points to add for joe-jobbed bounces
$sa_mail_body_size_limit = 400*1024; # don't waste time on SA if mail is larger
$sa_local_tests_only = 0; # only tests which do not require internet access?
# @lookup_sql_dsn =
# ( ['DBI:mysql:database=mail;host=127.0.0.1;port=3306', 'user1', 'passwd1'],
# ['DBI:mysql:database=mail;host=host2', 'username2', 'password2'],
# ["DBI:SQLite:dbname=$MYHOME/sql/mail_prefs.sqlite", '', ''] );
# @storage_sql_dsn = @lookup_sql_dsn; # none, same, or separate database
# @storage_redis_dsn = ( {server=>'127.0.0.1:6379', db_id=>1} );
# $redis_logging_key = 'amavis-log';
# $redis_logging_queue_size_limit = 300000; # about 250 MB / 100000
# $timestamp_fmt_mysql = 1; # if using MySQL *and* msgs.time_iso is TIMESTAMP;
# defaults to 0, which is good for non-MySQL or if msgs.time_iso is CHAR(16)
#$virus_admin = undef; # notifications recip.
$mailfrom_notify_admin = undef; # notifications sender
$mailfrom_notify_recip = undef; # notifications sender
$mailfrom_notify_spamadmin = undef; # notifications sender
$mailfrom_to_quarantine = ''; # null return path; uses original sender if undef
@addr_extension_virus_maps = ('virus');
@addr_extension_banned_maps = ('banned');
@addr_extension_spam_maps = ('spam');
@addr_extension_bad_header_maps = ('badh');
# $recipient_delimiter = '+'; # undef disables address extensions altogether
# when enabling addr extensions do also Postfix/main.cf: recipient_delimiter=+
$path = '/usr/local/sbin:/usr/local/bin:/usr/sbin:/sbin:/usr/bin:/bin';
# $dspam = 'dspam';
$MAXLEVELS = 14;
$MAXFILES = 3000;
$MIN_EXPANSION_QUOTA = 100*1024; # bytes (default undef, not enforced)
$MAX_EXPANSION_QUOTA = 500*1024*1024; # bytes (default undef, not enforced)
$sa_spam_subject_tag = '***Spam*** ';
$defang_virus = 1; # MIME-wrap passed infected mail
$defang_banned = 1; # MIME-wrap passed mail containing banned name
# for defanging bad headers only turn on certain minor contents categories:
$defang_by_ccat{CC_BADH.",3"} = 1; # NUL or CR character in header
$defang_by_ccat{CC_BADH.",5"} = 1; # header line longer than 998 characters
$defang_by_ccat{CC_BADH.",6"} = 1; # header field syntax error
# OTHER MORE COMMON SETTINGS (defaults may suffice):
# $myhostname = 'host.example.com'; # must be a fully-qualified domain name!
$myhostname = 'smtp.kamata-net.com'; # must be a fully-qualified domain name!
# The default forwarding port in the Fedora and RHEL SELinux policy is 10025.
# To allow additional ports you need to label them as 'amavisd_send_port_t'.
# For example: semanage port -a -t amavisd_send_port_t -p tcp 10023
# $notify_method = 'smtp:[127.0.0.1]:10023';
# $forward_method = 'smtp:[127.0.0.1]:10023'; # set to undef with milter!
$final_virus_destiny = D_DISCARD;
$final_banned_destiny = D_BOUNCE;
$final_spam_destiny = D_DISCARD; #!!! D_DISCARD / D_REJECT
$final_bad_header_destiny = D_BOUNCE;
# $bad_header_quarantine_method = undef;
| 12行目 | #@bypass_virus_checks_maps = (1); | Virusチェックをバイパスする指定(つまりウィルスチェックしない)ですのでコメントアウトされていることを確認してください。 |
| 13行目 | #@bypass_spam_checks_maps = (1); | スパムメールチェックをバイパスする指定ですのでコメントアウトされているこを確認してください。 |
| 23行目 | $mydomain = 'smtp.kamata-net.com'; | 自ドメインを指定します |
| 56-57行目 | @mynetworks | 信頼するLANアドレスの記載をします。IPv6アドレスについても[]で囲って記載可能です。 |
| 101-102行目 | $sa_tag_level_deflt = -999; | SpamAssassinで必ずX-Spam-Statusなどのヘッダを出力するための設定です。スコアが−999以上のときにヘッダを付加するようにしています |
| 161行目 | $myhostname = 'mail.kamata-net.com'; | 自身のホスト名 |
| 169行目 | $final_virus_destiny = D_DISCARD; | ウィルスメールは破棄します |
12行目、13行目のbypassについてはネット上ではコメントアウトを外すように記載されている記事が多いですが、これは間違いだと思います。コメントアウトを外してしまうと処理をバイパスされてしまいますのでご注意ください。私の環境では少なくともコメントアウトを外してbypassを有効にすると処理がされません。
自動起動されるようにします。
# systemctl start amavisd # systemctl enable amavisd Created symlink /etc/systemd/system/multi-user.target.wants/amavisd.service → /usr/lib/systemd/system/amavisd.service. #
Postfix
/etc/postfix/main.cf
content_filter = smtp-amavis:[127.0.0.1]:10024
を追加します。
また、/etc/postfix/master.cf
smtp-amavis unix - - n - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
を追加します。
設定ファイルをリロードします。
# postfix reload
SpamAssassin
インストール
SpamAssassinをインストールします。
# dnf install spamassassin メタデータの期限切れの最終確認: 0:00:58 時間前の 2021年02月03日 19時37分45秒 に実施しました。 依存関係が解決しました。 ========================================================================================================================================================================================= パッケージ アーキテクチャー バージョン リポジトリー サイズ ========================================================================================================================================================================================= インストール: spamassassin x86_64 3.4.2-10.el8 appstream 1.2 M 依存関係のインストール: perl-Algorithm-Diff noarch 1.1903-9.el8 baseos 52 k perl-Archive-Tar noarch 2.30-1.el8 baseos 79 k perl-Compress-Raw-Bzip2 x86_64 2.081-1.el8 baseos 40 k perl-Compress-Raw-Zlib x86_64 2.081-1.el8 baseos 68 k perl-Crypt-OpenSSL-Bignum x86_64 0.09-5.el8 appstream 46 k perl-Crypt-OpenSSL-RSA x86_64 0.31-1.el8 appstream 47 k perl-Crypt-OpenSSL-Random x86_64 0.15-3.el8 appstream 31 k perl-DB_File x86_64 1.842-1.el8 appstream 83 k perl-Data-Dump noarch 1.23-7.module_el8.3.0+416+dee7bcef appstream 37 k perl-Digest-HMAC noarch 1.03-17.module_el8.3.0+416+dee7bcef appstream 20 k perl-Digest-SHA x86_64 1:6.02-1.el8 appstream 66 k perl-Encode-Detect x86_64 1.01-28.el8 appstream 90 k perl-Encode-Locale noarch 1.05-10.module_el8.3.0+416+dee7bcef appstream 22 k perl-Error noarch 1:0.17025-2.el8 appstream 46 k perl-File-Listing noarch 6.04-17.module_el8.3.0+416+dee7bcef appstream 18 k perl-HTML-Parser x86_64 3.72-15.module_el8.3.0+416+dee7bcef appstream 119 k perl-HTML-Tagset noarch 3.20-34.module_el8.3.0+416+dee7bcef appstream 24 k perl-HTTP-Cookies noarch 6.04-2.module_el8.3.0+416+dee7bcef appstream 39 k perl-HTTP-Date noarch 6.02-19.module_el8.3.0+416+dee7bcef appstream 19 k perl-HTTP-Message noarch 6.18-1.module_el8.3.0+416+dee7bcef appstream 100 k perl-HTTP-Negotiate noarch 6.01-19.module_el8.3.0+416+dee7bcef appstream 22 k perl-IO-Compress noarch 2.081-1.el8 baseos 258 k perl-IO-HTML noarch 1.001-11.module_el8.3.0+416+dee7bcef appstream 28 k perl-IO-Socket-INET6 noarch 2.72-12.el8 appstream 33 k perl-IO-Zlib noarch 1:1.10-416.el8 baseos 80 k perl-LWP-MediaTypes noarch 6.02-15.module_el8.3.0+416+dee7bcef appstream 29 k perl-Mail-DKIM noarch 0.54-1.el8 appstream 162 k perl-Mail-SPF noarch 2.9.0-15.el8 appstream 153 k perl-MailTools noarch 2.20-2.el8 appstream 113 k perl-NTLM noarch 1.09-17.module_el8.3.0+416+dee7bcef appstream 24 k perl-Net-DNS noarch 1.15-1.el8 appstream 369 k perl-Net-HTTP noarch 6.17-2.module_el8.3.0+416+dee7bcef appstream 43 k perl-Net-SMTP-SSL noarch 1.04-5.el8 appstream 15 k perl-NetAddr-IP x86_64 4.079-7.el8 appstream 132 k perl-Socket6 x86_64 0.28-6.el8 appstream 36 k perl-Sys-Syslog x86_64 0.35-397.el8 appstream 50 k perl-Text-Diff noarch 1.45-2.el8 baseos 45 k perl-Time-HiRes x86_64 1.9758-1.el8 appstream 61 k perl-TimeDate noarch 1:2.30-15.module_el8.3.0+416+dee7bcef appstream 53 k perl-Try-Tiny noarch 0.30-7.module_el8.3.0+416+dee7bcef appstream 45 k perl-WWW-RobotRules noarch 6.02-18.module_el8.3.0+416+dee7bcef appstream 23 k perl-libwww-perl noarch 6.34-1.module_el8.3.0+416+dee7bcef appstream 212 k perl-version x86_64 6:0.99.24-1.el8 appstream 67 k トランザクションの概要 ========================================================================================================================================================================================= インストール 44 パッケージ ダウンロードサイズの合計: 4.2 M インストール済みのサイズ: 9.8 M これでよろしいですか? [y/N]: y 〜〜
設定
/etc/mail/spamassassin/v310.preを編集します。
# TextCat - language guesser
#
loadplugin Mail::SpamAssassin::Plugin::TextCat
上記のコメントアウトを外して日本語に対応するようにします。
/etc/mail/spamassassin/local.cfを編集します。すでに秘伝のタレのようになっていますが…。http://www.flcl.org/~yoh/user_prefs をダウンロードしてlocal.cfにコピーして使うといいのですが、現在はダウンロードできなくなっているようです。
| blacklist_from | 指定したメールアドレスをブラックリストとして扱います | blacklist_from *@*.ar blacklist_from *@*.au blacklist_from *@*.br blacklist_from *@*.ca blacklist_from *@*.cc #blacklist_from *@*.cn blacklist_from *@*.cz blacklist_from *@*.de blacklist_from *@*.dk blacklist_from *@*.edu blacklist_from *@*.es blacklist_from *@*.fr #blacklist_from *@*.fi blacklist_from *@*.gov blacklist_from *@*.it blacklist_from *@*.kr blacklist_from *@*.mx blacklist_from *@*.me blacklist_from *@*.nl blacklist_from *@*.no blacklist_from *@*.nu blacklist_from *@*.pt blacklist_from *@*.ph blacklist_from *@*.ru blacklist_from *@*.sc blacklist_from *@*.th blacklist_from *@*.tw blacklist_from *@*.uk blacklist_from *@*.za blacklist_from *@*.xyz blacklist_from *@*.co blacklist_from *@*.hu blacklist_from *@*.vn blacklist_from *@*.ru blacklist_from *@*.at blacklist_from *@*.ca blacklist_from *@*.il blacklist_from *@*.link blacklist_from *@*.click blacklist_from *@*.space blacklist_from *@*.date blacklist_from *@*.host |
| whitelist_from_dkim | DKIMチェックをpassしたメールアドレスのうち指定されたアドレスを無条件に通過させます | whitelist_from_dkim *@*.co.jp |
| whitelist_from_spf | SPFチェックをpassしたメールアドrすのうち指定されたアドレスを無条件に通過させます | whitelist_from_spf *@*.go.jp whitelist_from_spf *@*.ac.jp |
| whitelist_from | 個別のホワイトリストです(Fromアドレスで判定) | whitelist_from *@fujissl.jp whitelist_from do_not_reply@line.me |
| whitelist_to |
個別のホワイトリストです(Toアドレスで判定) 主にメーリングリストなどで指定するのに使っています |
whitelist_to (メーリングリストアドレス) |
続いて自動起動設定です。
# systemctl start spamassassin # systemctl enable spamassassin Created symlink /etc/systemd/system/multi-user.target.wants/spamassassin.service → /usr/lib/systemd/system/spamassassin.service. #
続いてspamassassinのルールが自動更新されるようにsa-update.serviceも自動起動登録します。
# systemctl start sa-update # systemctl enable sa-update The unit files have no installation config (WantedBy, RequiredBy, Also, Alias settings in the [Install] section, and DefaultInstance for template units). This means they are not meant to be enabled using systemctl. Possible reasons for having this kind of units are: 1) A unit may be statically enabled by being symlinked from another unit's .wants/ or .requires/ directory. 2) A unit's purpose may be to act as a helper for some other unit which has a requirement dependency on it. 3) A unit may be started when needed via activation (socket, path, timer, D-Bus, udev, scripted systemctl call, ...). 4) In case of template units, the unit is meant to be enabled with some instance name specified. #
上記のようにエラーメッセージが表示されました。/usr/lib/systemd/system/sa-update.serviceファイルの内容に不備があるようなので修正します。
### Spamassassin Rules Updates ###
#
# http://wiki.apache.org/spamassassin/RuleUpdates
#
# sa-update automatically updates your rules once per day if a spam daemon like
# spamd or amavisd are running.
[Unit]
Description=Spamassassin Rules Update
Documentation=man:sa-update(1)
[Service]
# Note that the opposite of "yes" is the empty string, NOT "no"
# Options for the actual sa-update command
# These are added to the channel configuration from
# /etc/mail/spamassassin/channel.d/*.conf
Environment=OPTIONS=-v
# Debug script - send mail even if no update available
#Environment=DEBUG=yes
# Send mail when updates successfully processed
# Default: send mail only on error
#Environment=NOTIFY_UPD=yes
ExecStart=/usr/share/spamassassin/sa-update.cron
SuccessExitStatus=1
[Install]
WantedBy = multi-user.target
上記30−31行目を追加しています。依存関係はありませんのであまり気にする必要はなく上記のコピペで問題ありません。
ClamAV
インストール
# dnf install clamd clamav-update 〜〜
設定
/etc/clamd.d配下に設定ファイルがありますが、基本的には何も変更しなくても大丈夫です。ログにタイムスタンプを入れたい、などの要望があれば変更してください。
また、パターンファイルの更新ジョブの登録が必要です。
/etc/cron.daily/freshclamとして以下のシェルスクリプトを格納します。
#!/bin/sh
/usr/bin/freshclam --daemon-notify --quiet --log=/var/log/freshclam.log
上記でも問題ないのですが、clamav-freshclam.serviceを登録することで1時間に1度チェックが走るようになりますのでこちらを利用することにします。
# systemctl start clamav-freshclam # systemctl enable clamav-freshclam Created symlink /etc/systemd/system/multi-user.target.wants/clamav-freshclam.service → /usr/lib/systemd/system/clamav-freshclam.service. #
また、ClamAVの自動起動設定を行います。
# systemctl start clamd@amavisd # systemctl enable clamd@amavisd Created symlink /etc/systemd/system/multi-user.target.wants/clamd@amavisd.service → /usr/lib/systemd/system/clamd@.service.
注意ポイント
- いろいろなサイトを見てclamd@scanを有効にするのはこの場合間違いです。
- clamd@scanはサーバー内のウィルスチェックでありメールのリアルタイムチェックではありません。
- clamd@scanとclamd@amavisdはそれぞれ別のプロセスが起動します。
ClamAVはネットでも騒がれていますが確かにメモリの使用率が高いですね。今後チューニングしていきたいと思います。
Pypolicyd-spf
インストール
# dnf install pypolicyd-spf メタデータの期限切れの最終確認: 0:37:32 時間前の 2021年02月03日 23時44分11秒 に実施しました。 依存関係が解決しました。 ========================================================================================================================================================================================= パッケージ アーキテクチャー バージョン リポジトリー サイズ ========================================================================================================================================================================================= インストール: pypolicyd-spf noarch 2.0.2-7.el8 epel 56 k 依存関係のインストール: python3-pip noarch 9.0.3-18.el8 appstream 20 k python3-py3dns noarch 3.2.1-1.el8 epel 50 k python3-pyspf noarch 2.0.14-8.el8 epel 56 k python3-setuptools noarch 39.2.0-6.el8 baseos 163 k python36 x86_64 3.6.8-2.module_el8.3.0+562+e162826a appstream 19 k モジュールストリームの有効化中: python36 3.6 トランザクションの概要 ========================================================================================================================================================================================= インストール 6 パッケージ ダウンロードサイズの合計: 363 k インストール済みのサイズ: 882 k これでよろしいですか? [y/N]: y ~~
設定
pypolicyd-spf
/etc/python-policyd-spf/policyd-spf.confを修正します。
"policyd-spf.conf" 15L, 302C 1,1 全て
# For a fully commented sample config file see policyd-spf.conf.commented
debugLevel = 1
TestOnly = 1
#HELO_reject = Fail
#Mail_From_reject = Fail
HELO_reject = False
Mail_From_reject = False
PermError_reject = False
TempError_Defer = False
skip_addresses = 127.0.0.0/8,::ffff:127.0.0.0/104,::1
| 7行目 | HELO_reject = False | Failでは破棄となってしまうのでここではチェックのみに留めます |
| 8行目 | Mail_From_reject = False | 同上 |
Postfix
/etc/postfix/main.cf
smtpd_recipient_restrictions =
permit_mynetworks
permit_sasl_authenticated
reject_unauth_destination
check_policy_service unix:private/policy-spf
5行目を追加します。
/etc/postfix/master.cfに以下の行を追加してください。
policy-spf unix - n n - 0 spawn user=nobody argv=/usr/bin/python3 /usr/libexec/postfix/policyd-spf /etc/python-policyd-spf/policyd-spf.conf
設定のリロードを行います。
# postfix reload
SMTP-AUTH設定
インストール
さて、どんどん行きましょう。SMTP-AUTHを実現するためのモジュールとしてcyrus-saslをインストールします。
# dnf install cyrus-sasl メタデータの期限切れの最終確認: 0:29:27 時間前の 2021年02月04日 20時58分28秒 に実施しました。 依存関係が解決しました。 ================================================================================================================================================================================ パッケージ アーキテクチャー バージョン リポジトリー サイズ ================================================================================================================================================================================ インストール: cyrus-sasl x86_64 2.1.27-5.el8 baseos 96 k トランザクションの概要 ================================================================================================================================================================================ インストール 1 パッケージ ダウンロードサイズの合計: 96 k インストール済みのサイズ: 150 k これでよろしいですか? [y/N]: y 〜〜
設定
/etc/sysconfig/saslauthdを以下のように編集します。
# Directory in which to place saslauthd's listening socket, pid file, and so
# on. This directory must already exist.
SOCKETDIR=/run/saslauthd
# Mechanism to use when checking passwords. Run "saslauthd -v" to get a list
# of which mechanism your installation was compiled with the ablity to use.
#MECH=pam
MECH=shadow
# Additional flags to pass to saslauthd on the command line. See saslauthd(8)
# for the list of accepted flags.
FLAGS=
動作確認
telnetでSMTP(25/tcp)に接続して確認します。
# printf "%s\0%s\0%s" test@kamata-net.com user password | openssl base64 -e | tr -d '\n'; echo dGVzdEBrYW1hdGEtbmV0LmNvbQB1c2VyAHBhc3N3b3Jk # telnet localhost 25 Trying ::1... Connected to localhost. Escape character is '^]'. 220 mail.kamata-net.com ESMTP EHLO localhost 250-mail.kamata-net.com 250-PIPELINING 250-SIZE 10240000 250-ETRN 250-STARTTLS 250-AUTH PLAIN LOGIN 250-AUTH=PLAIN LOGIN 250-ENHANCEDSTATUSCODES 250-8BITMIME 250-DSN 250 SMTPUTF8 AUTH LOGIN dGVzdEBrYW1hdGEtbmV0LmNvbQB1c2VyAHBhc3N3b3Jk 334 UGFzc3dvcmQ6
エラーが出なければOKです。
SMTP over SSL(SMTPS)の設定
iPhoneやWindowsのOutlookからの接続するためにSMTPSとIMAPSを設定します。まずはSMTPSから。
opensslを使ってオレオレ認証局とそのオレオレ認証局で署名したオレオレ証明書を作成していきます。
自己認証局(CA)の作成
自己認証局の秘密鍵作成
/etc/pki/tls配下にすでにいろいろと格納されているのですが、ここは何が参照しているのか不明なため、/etc/pki/配下に新たにCAと証明書類を格納していくこととします。
# cd /etc/pki # mkdir postfix # cd postfix # mkdir private certs newcerts crl # cp ../tls/openssl.ca.cnf . # touch index.txt # echo "00" > serial
/etc/pki/postfix/openssl.ca.cnfを自己認証局用に編集していきます。
〜〜
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = JP
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Tokyo
localityName = Locality Name (eg, city)
localityName_default = Ota-ku
0.organizationName = Organization Name (eg, company)
0.organizationName_default = Kamata-Net
# we can do this but it is not needed normally :-)
#1.organizationName = Second Organization Name (eg, company)
#1.organizationName_default = World Wide Web Pty Ltd
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = CA (Certification Authority)
commonName = Common Name (eg, your name or your server\'s hostname)
commonName_default = CA.kamata-net.com
commonName_max = 64
emailAddress = Email Address
emailAddress_default = webmaster@kamata-net.com
emailAddress_max = 64
# SET-ex3 = SET extension number 3
[ req_attributes ]
challengePassword = A challenge password
challengePassword_min = 4
challengePassword_max = 20
unstructuredName = An optional company name
[ usr_cert ]
# These extensions are added when 'ca' signs a request.
# This goes against PKIX guidelines but some CAs do it and some software
# requires this to avoid interpreting an end user certificate as a CA.
#basicConstraints=CA:FALSE
basicConstraints=CA:TRUE
# Here are some examples of the usage of nsCertType. If it is omitted
# the certificate can be used for anything *except* object signing.
# This is OK for an SSL server.
# nsCertType = server
# For an object signing certificate this would be used.
# nsCertType = objsign
# For normal client use this is typical
# nsCertType = client, email
nsCertType = client, email
〜〜
| 171、175行目 | デフォルトの値を設定しておきます | エントリーが無かったので追加しています。 |
| 194、195,行目 | CA証明書の場合はCA:Trueが必須です | |
| 207、208行目 | 今回はサーバー証明書ではなくmail用途なので変更しておきます | 必須かどうか不明…。 |
さて、CA用の公開鍵、秘密鍵のキーペアを作成します。
# openssl genrsa -aes256 -out /etc/pki/postfix/private/cakey.pem 4096 Generating RSA private key, 4096 bit long modulus (2 primes) ...............................++++ ........++++ e is 65537 (0x010001) Enter pass phrase for /etc/pki/postfix/private/cakey.pem:★パスフレーズ入力 Verifying - Enter pass phrase for /etc/pki/postfix/private/cakey.pem: #
証明書発行要求 CSRファイル 作成
コマンドを入力してパスフレーズを入れたらエンターのみ押していけば問題ありません。
# openssl req -config ./openssl.ca.cnf -new -key /etc/pki/postfix/private/cakey.pem -out /etc/pki/postfix/cacert.csr Enter pass phrase for /etc/pki/postfix/private/cakey.pem:★設定したパスフレーズを入力 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [JP]: State or Province Name (full name) [Tokyo]: Locality Name (eg, city) [Ota-ku]: Organization Name (eg, company) [Kamata-Net]: Organizational Unit Name (eg, section) [CA (Certification Authority)]: Common Name (eg, your name or your server's hostname) [CA.kamata-net.com]: Email Address [webmaster@kamata-net.com]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:★入力しない。エンターのみ An optional company name []:★入力しない。エンターのみ #
自己認証局用証明書発行
認証局証明書の有効期限は3650日(10年)で作ります。
# openssl x509 -days 3650 -in /etc/pki/postfix/cacert.csr -req -signkey /etc/pki/postfix/private/cakey.pem -out /etc/pki/postfix/cacert.pem Signature ok subject=C = JP, ST = Tokyo, L = Ota-ku, O = Kamata-Net, OU = CA (Certification Authority), CN = CA.kamata-net.com, emailAddress = webmaster@kamata-net.com Getting Private key Enter pass phrase for /etc/pki/postfix/private/cakey.pem: # ls -al 合計 28 drwxr-xr-x 6 root root 164 2月 5 01:24 . drwxr-xr-x. 14 root root 191 2月 5 00:04 .. -rw-r--r-- 1 root root 1781 2月 5 01:26 cacert.csr -rw-r--r-- 1 root root 2078 2月 5 01:27 cacert.pem drwxr-xr-x 2 root root 43 2月 5 01:06 certs drwxr-xr-x 2 root root 6 2月 5 00:22 crl -rw-r--r-- 1 root root 3 2月 5 00:46 crlnumber -rw-r--r-- 1 root root 0 2月 5 00:22 index.txt drwxr-xr-x 2 root root 6 2月 5 00:22 newcerts -rw-r--r-- 1 root root 11433 2月 5 01:24 openssl.cnf drwxr-xr-x 2 root root 42 2月 5 00:58 private -rw-r--r-- 1 root root 3 2月 5 00:22 serial #
作成したルート証明書、cacert.pemを見てみましょう。
# openssl x509 -in cacert.pem -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
3e:e6:78:aa:5d:cd:34:3c:c3:ba:1f:6d:f7:b2:2e:6c:07:8b:55:97
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = JP, ST = Tokyo, L = Ota-ku, O = Kamata-Net, OU = CA (Certification Authority)
Validity
Not Before: Feb 4 15:53:59 2021 GMT
Not After : Feb 2 15:53:59 2031 GMT
Subject: C = JP, ST = Tokyo, L = Ota-ku, O = Kamata-Net, OU = CA (Certification Authority)
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (4096 bit)
Modulus:
00:cd:94:98:61:2e:92:32:0f:50:72:c9:9a:a1:3d:
〜〜
Postfix用の証明書作成
続いて、Postfix用の証明書を作成していきます。
秘密鍵作成
/etc/postfix/main.cfを見ると、パスフレーズなしでアクセスできる必要があるとのことです。
# The full pathname of a file with the Postfix SMTP server RSA private key
# in PEM format. The private key must be accessible without a pass-phrase,
# i.e. it must not be encrypted.
#
ですのでパスフレーズなしでキーペアの作成を行います。
# openssl genrsa -out /etc/pki/postfix/private/privkey.pem 4096 Generating RSA private key, 4096 bit long modulus (2 primes) ......................................................................................................++++ .............++++ e is 65537 (0x010001) #
証明書発行要求 CSR 作成
# openssl req -config ./openssl.smtp.cnf -new -key /etc/pki/postfix/private/privkey.pem -out /etc/pki/postfix/certs/postfix.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [JP]: State or Province Name (full name) [Tokyo]: Locality Name (eg, city) [Ota-ku]: Organization Name (eg, company) [Kamata-Net]: Organizational Unit Name (eg, section) [Blog.Kamata-Net.Com]: Common Name (eg, your name or your server's hostname) [mail.kamata-net.com]: Email Address [webmaster@kamata-net.com]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: [root@kamatans postfix]#
おわかりの通り、openssl.ca.cnfをopenssl.smtp.cnfにコピーして使っています。
証明書発行
# openssl ca -config ./openssl.smtp.cnf -in /etc/pki/postfix/certs/postfix.csr -out /etc/pki/postfix/certs/postfix.pem -days 3650
Using configuration from ./openssl.smtp.cnf
Enter pass phrase for /etc/pki/postfix/private/cakey.pem: ★CA証明書で設定したパスフレーズを入力します
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Feb 4 16:30:19 2021 GMT
Not After : Feb 2 16:30:19 2031 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
organizationName = Kamata-Net
organizationalUnitName = Blog.Kamata-Net.Com
commonName = mail.kamata-net.com
emailAddress = webmaster@kamata-net.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:TRUE
Netscape Cert Type:
SSL Client, S/MIME
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
11:96:E8:FE:42:1A:05:14:52:73:0D:31:7D:D5:16:08:77:B9:14:0A
X509v3 Authority Key Identifier:
DirName:/C=JP/ST=Tokyo/L=Ota-ku/O=Kamata-Net/OU=Blog.Kamata-Net.Com/CN=mail.kamata-net.com/emailAddress=webmaster@kamata-net.com
serial:09:ED:2D:C9:6F:33:CF:1D:63:E3:8C:4D:88:2E:1C:23:E4:67:CB:B3
Certificate is to be certified until Feb 2 16:30:19 2031 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
#
Postfix設定
/etc/postfix/main.cfを編集します。
# TLS CONFIGURATION
#
# Basic Postfix TLS configuration by default with self-signed certificate
# for inbound SMTP and also opportunistic TLS for outbound SMTP.
# The full pathname of a file with the Postfix SMTP server RSA certificate
# in PEM format. Intermediate certificates should be included in general,
# the server certificate first, then the issuing CA(s) (bottom-up order).
#
smtpd_tls_cert_file = /etc/pki/postfix/certs/postfix.pem
# The full pathname of a file with the Postfix SMTP server RSA private key
# in PEM format. The private key must be accessible without a pass-phrase,
# i.e. it must not be encrypted.
#
smtpd_tls_key_file = /etc/pki/postfix/private/privkey.pem
# Announce STARTTLS support to remote SMTP clients, but do not require that
# clients use TLS encryption (opportunistic TLS inbound).
#
smtpd_tls_security_level = may
# Directory with PEM format Certification Authority certificates that the
# Postfix SMTP client uses to verify a remote SMTP server certificate.
#
smtp_tls_CApath = /etc/pki/postfix/certs
# The full pathname of a file containing CA certificates of root CAs
# trusted to sign either remote SMTP server certificates or intermediate CA
# certificates.
#
#smtp_tls_CAfile = /etc/pki/postfix/certs/ca-bundle.crt
smtp_tls_CAfile = /etc/pki/postfix/cacert.pem
# Use TLS if this is supported by the remote SMTP server, otherwise use
# plaintext (opportunistic TLS outbound).
#
meta_directory = /etc/postfix
shlib_directory = /usr/lib64/postfix
環境に合わせてパスの設定をします。
さらに、以下の設定が必要です。
# SMTP-Auth
# SASL認証有効化
#自身のSMTP-AUTH化
smtpd_sasl_auth_enable = yes
#接続先(Submission用)のSMTP-AUTH
smtp_sasl_auth_enable = yes
# mynetworks以外で匿名での接続を拒否
smtpd_sasl_security_options = noanonymous
smtp_sasl_security_options = noanonymous
# 規格外の動作に対応
broken_sasl_auth_clients = yes
#SMTP-Auth User:Password
smtp_sasl_password_maps = hash:/etc/postfix/relay_password
ややこしいのですが(はまりました)、smtpd_xxxxxは自身がSMTP-AUTH認証を行う場合、smtp_xxxxは外部のメールサーバーのサブミッションポートなどにSMTP-AUTHで接続する場合の設定になります。
実は直接メールを配送するとスパムで弾かれてしまうケースが多々あり、私の家ではAsahi-netのメールサーバにほぼリレーしています。
-

-
ISPのメールサーバを使う場合のSPFレコード(asahi-netの場合)
自メールサーバではなくISPのメールサーバにリレーしてメールを配信している場合のSPF公開レコードの設定方法についてのご紹介。@setoatuはasa …続きを見る
-

-
Yahoo!メールで迷惑メールとして判定されてしまう件
Yahoo!メールに送ったメールが迷惑フォルダに振分けられているのを発見。X-YahooFilteredBulkというヘッダが問題のようなのでYaho …続きを見る
Asahi-netではサブミッションポートを用意しておりSMTP-AUTHが必要となります。ちなみに、relay_passwordの設定は以下のようになっています。
/etc/postfix/relay_password
[mail.asahi-net.or.jp]:587 (ユーザー名):(パスワード)
接続先のポートは、サブミッションポート(587/tcp)ですのでホスト名を[]:ポート番号と記述します。
# cd /etc/postfix # portmap relay_password # postfix reload
として、設定をDB化しPostfixの設定リロードを行います。
IMAP over SSL(IMAPS)の設定
Dovecotの設定
さて、続いてIMAPSの設定です。Dovecotで実現します。
/etc/dovecot/conf.d/10-mail.conf
##
## Mailbox locations and namespaces
##
# Location for users' mailboxes. The default is empty, which means that Dovecot
# tries to find the mailboxes automatically. This won't work if the user
# doesn't yet have any mail, so you should explicitly tell Dovecot the full
# location.
#
# If you're using mbox, giving a path to the INBOX file (eg. /var/mail/%u)
# isn't enough. You'll also need to tell Dovecot where the other mailboxes are
# kept. This is called the "root mail directory", and it must be the first
# path given in the mail_location setting.
#
# There are a few special variables you can use, eg.:
#
# %u - username
# %n - user part in user@domain, same as %u if there's no domain
# %d - domain part in user@domain, empty if there's no domain
# %h - home directory
#
# See doc/wiki/Variables.txt for full list. Some examples:
#
# mail_location = maildir:~/Maildir
# mail_location = mbox:~/mail:INBOX=/var/mail/%u
# mail_location = mbox:/var/mail/%d/%1n/%n:INDEX=/var/indexes/%d/%1n/%n
#
# <doc/wiki/MailLocation.txt>
#
mail_location = maildir:~/Maildir
一応おさらいですが、メールボックスの形式はMaildir形式としています。
#default_process_limit = 100
#default_client_limit = 1000
# Default VSZ (virtual memory size) limit for service processes. This is mainly
# intended to catch and kill processes that leak memory before they eat up
# everything.
#default_vsz_limit = 256M
# Login user is internally used by login processes. This is the most untrusted
# user in Dovecot system. It shouldn't have access to anything at all.
#default_login_user = dovenull
# Internal user is used by unprivileged processes. It should be separate from
# login user, so that login processes can't disturb other processes.
#default_internal_user = dovecot
service imap-login {
inet_listener imap {
#port = 143
}
inet_listener imaps {
port = 993
ssl = yes
}
993/tcpをListenします。
##
## SSL settings
##
# SSL/TLS support: yes, no, required. <doc/wiki/SSL.txt>
# disable plain pop3 and imap, allowed are only pop3+TLS, pop3s, imap+TLS and imaps
# plain imap and pop3 are still allowed for local connections
ssl = required
# PEM encoded X.509 SSL/TLS certificate and private key. They're opened before
# dropping root privileges, so keep the key file unreadable by anyone but
# root. Included doc/mkcert.sh can be used to easily generate self-signed
# certificate, just make sure to update the domains in dovecot-openssl.cnf
#ssl_cert = </etc/pki/dovecot/certs/dovecot.pem
#ssl_key = </etc/pki/dovecot/private/dovecot.pem
ssl_cert = </etc/pki/postfix/certs/dovecot.pem
ssl_key = </etc/pki/postfix/private/dovecot.pem
dovecot用の証明書をPostfixと同様に作成して配置しています。もちろん先程作った/etc/pki/postfix/certs/postfix.pem、/etc/pki/postfix/private/privkey.pemを指定しても構いません。
動作確認
opensslコマンドを用いて接続確認を行います。
# openssl s_client -connect mail.kamata-net.com:993
CONNECTED(00000003)
depth=0 C = JP, ST = Tokyo, O = Kamata-Net, OU = Blog.Kamata-Net.Com, CN = mail.kamata-net.com, emailAddress = webmaster@kamata-net.com
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = JP, ST = Tokyo, O = Kamata-Net, OU = Blog.Kamata-Net.Com, CN = mail.kamata-net.com, emailAddress = webmaster@kamata-net.com
verify error:num=26:unsupported certificate purpose
verify return:1
depth=0 C = JP, ST = Tokyo, O = Kamata-Net, OU = Blog.Kamata-Net.Com, CN = mail.kamata-net.com, emailAddress = webmaster@kamata-net.com
verify error:num=21:unable to verify the first certificate
verify return:1
---
Certificate chain
0 s:C = JP, ST = Tokyo, O = Kamata-Net, OU = Blog.Kamata-Net.Com, CN = mail.kamata-net.com, emailAddress = webmaster@kamata-net.com
i:C = JP, ST = Tokyo, L = Ota-ku, O = Kamata-Net, OU = CA (Certification Authority), CN = CA.kamata-net.com, emailAddress = webmaster@kamata-net.com
---
Server certificate
-----BEGIN CERTIFICATE-----
〜〜
---
read R BLOCK
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ AUTH=PLAIN] Dovecot ready.
1 login "(ユーザー名)" "(パスワード)"
1 OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SNIPPET=FUZZY PREVIEW=FUZZY LITERAL+ NOTIFY SPECIAL-USE] Logged in
2 list "" *
* LIST (\HasNoChildren \UnMarked) "." &Tgtm+DBN-
* LIST (\HasNoChildren \UnMarked) "." &j,dg0TDhMPww6w-
* LIST (\HasNoChildren \UnMarked) "." Notes
* LIST (\HasNoChildren \UnMarked \Sent) "." Sent
* LIST (\HasNoChildren \UnMarked \Junk) "." Junk
* LIST (\HasNoChildren \UnMarked) "." FaceBook
* LIST (\HasNoChildren \UnMarked \Drafts) "." Drafts
* LIST (\HasNoChildren \UnMarked) "." Archive
* LIST (\HasNoChildren \UnMarked) "." LS
* LIST (\HasNoChildren \UnMarked \Trash) "." Trash
* LIST (\HasNoChildren) "." INBOX
2 OK List completed (0.001 + 0.000 secs).
select INBOX
select BAD Error in IMAP command INBOX: Unknown command (0.001 + 0.000 secs).
3 select INBOX
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 1230 EXISTS
* 0 RECENT
* OK [UNSEEN 1220] First unseen.
* OK [UIDVALIDITY 1612527330] UIDs valid
* OK [UIDNEXT 1250] Predicted next UID
* OK [HIGHESTMODSEQ 79] Highest
3 OK [READ-WRITE] Select completed (0.002 + 0.000 + 0.001 secs).
4 fetch 1 body[]
* 1 FETCH (BODY[] {42039}
Received: (qmail 30054 invoked by alias); 6 Dec 2020 09:41:40 +0900
〜〜
ファイアウォールの設定
ここまで来たら外部から接続できるようにファイアウォールに穴あけをしておきます。
# firewalld-cmd --permanent --add-service=smtp # firewalld-cmd --permanent --add-service=smtps # firewalld-cmd --permanent --add-service=imaps # systemctl reload firewalld
DKIM設定
DKIM署名とチェックをするための設定です。opendkimを利用して実現します。
インストール
# dnf install opendkim 〜〜
公開鍵・秘密鍵ペアの作成
# cd /etc/opendkim/keys # mkdir kamata-net.com # opendkim-genkey -D /etc/opendkim/keys/kamata-net.com -d kamata-net.com -s default # chown -R opendkim:opendkim .
defaultとなっているのはセパレータなのでどんな文字列でも構いませんが、DNSで公開することになりますので恥ずかしいセパレータ名にするのはやめましょう。defaultが一般的なセパレータ名です。
設定
opendkim
/etc/opendkim/KeyTableで秘密鍵の格納場所を指定します。複数のドメインを運用している場合にはすべてこちらの記載します。
"KeyTable" 11L, 847C 1,1 全て
# OPENDKIM KEY TABLE
# To use this file, uncomment the #KeyTable option in /etc/opendkim.conf,
# then uncomment the following line and replace example.com with your domain
# name, then restart OpenDKIM. Additional keys may be added on separate lines.
#default._domainkey.example.com example.com:default:/etc/opendkim/keys/default.private
default._domainkey.kamata-net.com kamata-net.com:default:/etc/opendkim/keys/kamata-net.com/default.private
default._domainkey.kamata-net.jp kamata-net.jp:default:/etc/opendkim/keys/kamata-net.jp/default.private
…
続いて、/etc/opendkim/SigningTableにて署名を行う対象のドメイン(というよりメールアドレス)を指定します。
"SigningTable" 30L, 1458C 1,1 全て
# OPENDKIM SIGNING TABLE
# This table controls how to apply one or more signatures to outgoing messages based
# on the address found in the From: header field. In simple terms, this tells
# OpenDKIM "how" to apply your keys.
# To use this file, uncomment the SigningTable option in /etc/opendkim.conf,
# then uncomment one of the usage examples below and replace example.com with your
# domain name, then restart OpenDKIM.
# WILDCARD EXAMPLE
# Enables signing for any address on the listed domain(s), but will work only if
# "refile:/etc/opendkim/SigningTable" is included in /etc/opendkim.conf.
# Create additional lines for additional domains.
#*@example.com default._domainkey.example.com
# NON-WILDCARD EXAMPLE
# If "file:" (instead of "refile:") is specified in /etc/opendkim.conf, then
# wildcards will not work. Instead, full user@host is checked first, then simply host,
# then user@.domain (with all superdomains checked in sequence, so "foo.example.com"
# would first check "user@foo.example.com", then "user@.example.com", then "user@.com"),
# then .domain, then user@*, and finally *. See the opendkim.conf(5) man page under
# "SigningTable" for more details.
#example.com default._domainkey.example.com
*@kamata-net.com default._domainkey.kamata-net.com
*@kamata-net.jp default._domainkey.kamata-net.jp
…
ちなみに
kamata-net.com default._domainkey.kamata-net.com
とドメイン指定したのですが、うまく署名してくれませんでした。
続いて信頼するホスト(接続を許可するアドレス)を/etc/opendkim/TrustedHostsファイルにて指定します。同一ホストのPostfixからの接続しかありませんのでループバックアドレスのみ記載しておきます。
"TrustedHosts" 9L, 378C 1,1 全て
# OPENDKIM TRUSTED HOSTS
# To use this file, uncomment the #ExternalIgnoreList and/or the #InternalHosts
# option in /etc/opendkim.conf then restart OpenDKIM. Additional hosts
# may be added on separate lines (IP addresses, hostnames, or CIDR ranges).
# The localhost IP (127.0.0.1) should always be the first entry in this file.
127.0.0.1
::1
#host.example.com
#192.168.1.0/24
Postfix
/etc/postfix/master.cfにDKIM署名の設定を追加します。
# DKIM署名
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = inet:localhost:8891
milter_default_action = accept
Amavisd-New
/etc/amavisd/amavisd.confにて51-52行目でAmavisによるDKIMチェック、DKIM署名を実行する指定がありますが、opendkimを使っていますのでここは不要です。1→0として無効化します。
$enable_db = 1; # enable use of BerkeleyDB/libdb (SNMP and nanny)
# $enable_zmq = 1; # enable use of ZeroMQ (SNMP and nanny)
$nanny_details_level = 2; # nanny verbosity: 1: traditional, 2: detailed
$enable_dkim_verification = 0; # enable DKIM signatures verification
$enable_dkim_signing = 0; # load DKIM signing code, keys defined by dkim_key
DNSレコードの作成
SPF、DKIM、DMARC用のレコードをDNSに登録します。また合わせてIPv6対応も実施しておきます(IPv6レコード、AAAAの追加)。
$TTL 3600
@ IN SOA ns.kamata-net.com. root.ns.kamata-net.com. (
2021020503 ; Serial
10800 ; Refresh 3 hours
1800 ; Retry 30 minutes
43200 ; Expire 12 hours
3600 ) ; Minimum 1 hour
;$origin kamata-net.com.
IN AAAA 2405:6580:27e0:1300:20c:29ff:fe91:e989
IN A 218.45.184.224
IN NS ns.kamata-net.com.
IN MX 10 mail.kamata-net.com.
IN TXT "v=spf1 +mx +include:spf-01.asahi-net.or.jp -all"
default._domainkey IN TXT "v=DKIM1;k=rsa;p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC9LVK7mIQmGdDPvdfUTZXnOlsaY0p4YMwDmuBK+vyQrH+V7fNULyGXn5nuMeRFbMKwos72Uuw4Af/YQ6ppGxRNrCdu7g8jnGGmMSU165xgNvLUKr/qjaoNdBK/8W5V7EhpEinKC5+9OeSeh5io24gLPZwIjeRTfiF5T3jW7eo6nQIDAQAB"
_adsp._domainkey IN TXT "dkim=all"
_dmarc IN TXT "v=DMARC1;p=none;rua=mailto:postmaster@kamata-net.com;ruf=mailto:postmaster@kamata-net.com;rf=afrf;pct=100"
;
;
mail IN A 218.45.184.224
mail IN AAAA 2405:6580:27e0:1300:d224:43aa:890a:f888
smtp IN A 218.45.184.224
smtp IN AAAA 2405:6580:27e0:1300:d224:43aa:890a:f888
imap IN A 218.45.184.224
imap IN AAAA 2405:6580:27e0:1300:d224:43aa:890a:f888
ns IN A 218.45.184.224
ns IN AAAA 2405:6580:27e0:1300:d224:43aa:890a:f888
static IN A 218.45.184.224
static IN AAAA 2405:6580:27e0:1300:20c:29ff:fe91:e989
blog IN A 218.45.184.224
blog IN AAAA 2405:6580:27e0:1300:20c:29ff:fe91:e989
blog IN TXT "google-site-verification: kAyWyOulCwAZZIBOSqgBZUmPcJ74T3nsEejnU58Ttw8"
blog IN MX 10 mail.kamata-net.com.
www IN A 218.45.184.224
www IN AAAA 2405:6580:27e0:1300:20c:29ff:fe91:e989
www IN TXT "google-site-verification: cyjBNfZDifARLZ1jrPNotZFmYk4KshcjGnppX59zN8Q"
old IN A 218.45.184.224
old IN AAAA 2405:6580:27e0:1300:20c:29ff:fe91:e989
sip IN A 218.45.184.224
;
;
localhost IN A 127.0.0.1
loghost IN CNAME localhost
|
14行目 |
SPF用レコード |
送信される可能性のあるホストを羅列します。自身(mx)とAsahi-net(include:spf-01.asahi-net.or.jp)以外はすべて拒否(-all)しています。 (※)下記の記事もご参考にどうぞ |
| 15行目 | DKIM用レコード | /etc/opendkim/keys/(ドメイン名)/default.txtの内容を記載します |
| 16行目 | DKIM用ADSPレコード(Author Domain Signing Practice) |
DKIMの認証結果をどのように扱うべきかを示すポリシーを送信側で公開するものです。 all: すべてのメールに署名が付与される unknown:いくつかのメールに署名が付与される discardable:署名が付いていなかったら破棄するように指示 |
| 17行目 | DMARC用レコード |
相手側メールホストにて実施されるDMARC認証に失敗した場合のポリシーの設定です。大事なのはポリシーを指定しているp=の部分です。 none:何もしない quarantine:隔離する reject:メール受信拒否 |
-

-
ISPのメールサーバを使う場合のSPFレコード(asahi-netの場合)
自メールサーバではなくISPのメールサーバにリレーしてメールを配信している場合のSPF公開レコードの設定方法についてのご紹介。@setoatuはasa …続きを見る
最終動作確認
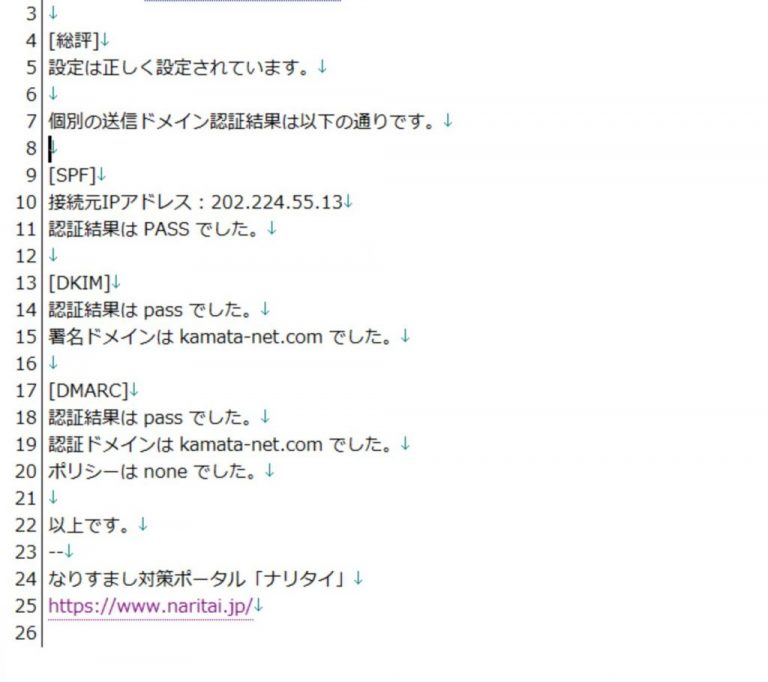
SPFレコードとDMARCレコードのチェックを行ってくれます。
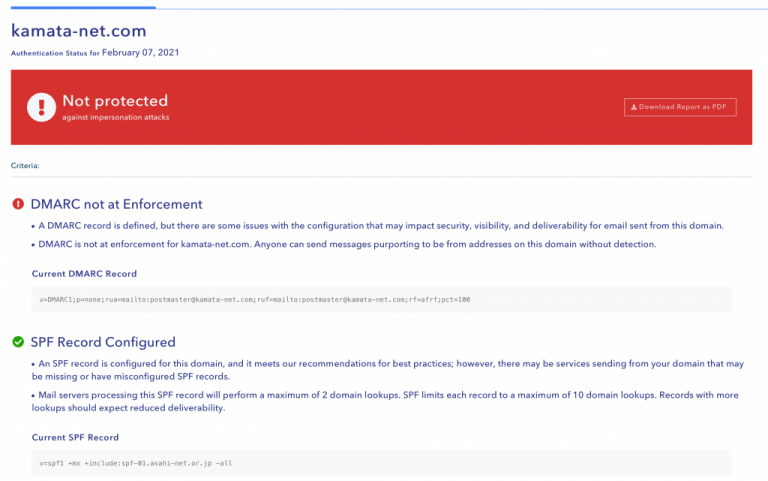
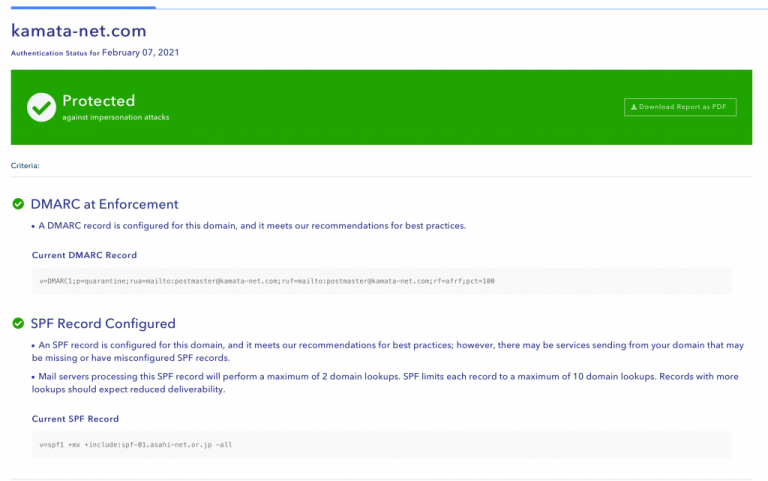
p=noneで設定していたのですが、これだと保護されていない、とのことなのでp=quarantine(隔離)に変更しました。
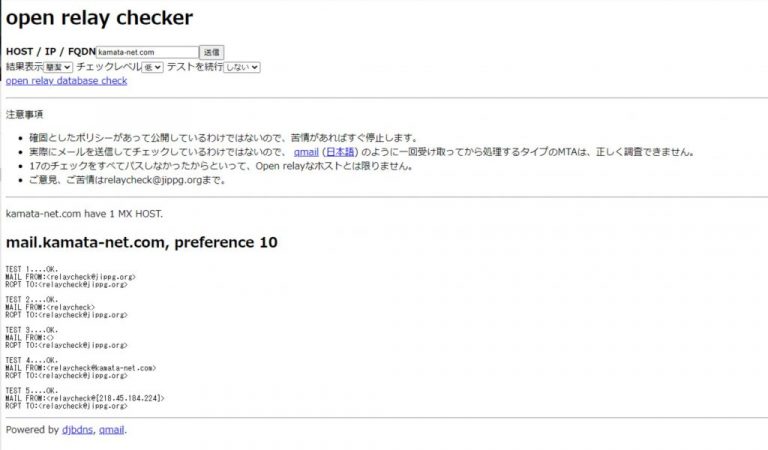
以下のサイトでは基本となるオープンリレーのチェックをしてくれます。踏み台サーバにならないように必ずチェックをしましょう。
以下のサイトでもチェックが可能です。シンプルにcheck@naritai.jpに空メールを送るだけで診断してもらえます。
参考資料(各種設定ファイル)
少々長くなりましたがいかがでしたでしょうか?参考になれば幸いです。最後に我が家のPostfix関連の設定ファイルを掲載致します。
Postfix
main.cf
# Global Postfix configuration file. This file lists only a subset
# of all parameters. For the syntax, and for a complete parameter
# list, see the postconf(5) manual page (command: "man 5 postconf").
#
# For common configuration examples, see BASIC_CONFIGURATION_README
# and STANDARD_CONFIGURATION_README. To find these documents, use
# the command "postconf html_directory readme_directory", or go to
# http://www.postfix.org/BASIC_CONFIGURATION_README.html etc.
#
# For best results, change no more than 2-3 parameters at a time,
# and test if Postfix still works after every change.
# COMPATIBILITY
#
# The compatibility_level determines what default settings Postfix
# will use for main.cf and master.cf settings. These defaults will
# change over time.
#
# To avoid breaking things, Postfix will use backwards-compatible
# default settings and log where it uses those old backwards-compatible
# default settings, until the system administrator has determined
# if any backwards-compatible default settings need to be made
# permanent in main.cf or master.cf.
#
# When this review is complete, update the compatibility_level setting
# below as recommended in the RELEASE_NOTES file.
#
# The level below is what should be used with new (not upgrade) installs.
#
compatibility_level = 2
# SOFT BOUNCE
#
# The soft_bounce parameter provides a limited safety net for
# testing. When soft_bounce is enabled, mail will remain queued that
# would otherwise bounce. This parameter disables locally-generated
# bounces, and prevents the SMTP server from rejecting mail permanently
# (by changing 5xx replies into 4xx replies). However, soft_bounce
# is no cure for address rewriting mistakes or mail routing mistakes.
#
#soft_bounce = no
# LOCAL PATHNAME INFORMATION
#
# The queue_directory specifies the location of the Postfix queue.
# This is also the root directory of Postfix daemons that run chrooted.
# See the files in examples/chroot-setup for setting up Postfix chroot
# environments on different UNIX systems.
#
queue_directory = /var/spool/postfix
# The command_directory parameter specifies the location of all
# postXXX commands.
#
command_directory = /usr/sbin
# The daemon_directory parameter specifies the location of all Postfix
# daemon programs (i.e. programs listed in the master.cf file). This
# directory must be owned by root.
#
daemon_directory = /usr/libexec/postfix
# The data_directory parameter specifies the location of Postfix-writable
# data files (caches, random numbers). This directory must be owned
# by the mail_owner account (see below).
#
data_directory = /var/lib/postfix
# QUEUE AND PROCESS OWNERSHIP
#
# The mail_owner parameter specifies the owner of the Postfix queue
# and of most Postfix daemon processes. Specify the name of a user
# account THAT DOES NOT SHARE ITS USER OR GROUP ID WITH OTHER ACCOUNTS
# AND THAT OWNS NO OTHER FILES OR PROCESSES ON THE SYSTEM. In
# particular, don't specify nobody or daemon. PLEASE USE A DEDICATED
# USER.
#
mail_owner = postfix
# The default_privs parameter specifies the default rights used by
# the local delivery agent for delivery to external file or command.
# These rights are used in the absence of a recipient user context.
# DO NOT SPECIFY A PRIVILEGED USER OR THE POSTFIX OWNER.
#
#default_privs = nobody
# INTERNET HOST AND DOMAIN NAMES
#
# The myhostname parameter specifies the internet hostname of this
# mail system. The default is to use the fully-qualified domain name
# from gethostname(). $myhostname is used as a default value for many
# other configuration parameters.
#
#myhostname = host.domain.tld
#myhostname = virtual.domain.tld
myhostname = mail.kamata-net.com
# The mydomain parameter specifies the local internet domain name.
# The default is to use $myhostname minus the first component.
# $mydomain is used as a default value for many other configuration
# parameters.
#
#mydomain = domain.tld
mydomain = kamata-ne.tcom
# SENDING MAIL
#
# The myorigin parameter specifies the domain that locally-posted
# mail appears to come from. The default is to append $myhostname,
# which is fine for small sites. If you run a domain with multiple
# machines, you should (1) change this to $mydomain and (2) set up
# a domain-wide alias database that aliases each user to
# user@that.users.mailhost.
#
# For the sake of consistency between sender and recipient addresses,
# myorigin also specifies the default domain name that is appended
# to recipient addresses that have no @domain part.
#
#myorigin = $myhostname
#myorigin = $mydomain
# RECEIVING MAIL
# The inet_interfaces parameter specifies the network interface
# addresses that this mail system receives mail on. By default,
# the software claims all active interfaces on the machine. The
# parameter also controls delivery of mail to user@[ip.address].
#
# See also the proxy_interfaces parameter, for network addresses that
# are forwarded to us via a proxy or network address translator.
#
# Note: you need to stop/start Postfix when this parameter changes.
#
#inet_interfaces = $myhostname
#inet_interfaces = $myhostname, localhost
inet_interfaces = all
#inet_interfaces = localhost
# Enable IPv4, and IPv6 if supported
inet_protocols = all
# The proxy_interfaces parameter specifies the network interface
# addresses that this mail system receives mail on by way of a
# proxy or network address translation unit. This setting extends
# the address list specified with the inet_interfaces parameter.
#
# You must specify your proxy/NAT addresses when your system is a
# backup MX host for other domains, otherwise mail delivery loops
# will happen when the primary MX host is down.
#
#proxy_interfaces =
#proxy_interfaces = 1.2.3.4
# The mydestination parameter specifies the list of domains that this
# machine considers itself the final destination for.
#
# These domains are routed to the delivery agent specified with the
# local_transport parameter setting. By default, that is the UNIX
# compatible delivery agent that lookups all recipients in /etc/passwd
# and /etc/aliases or their equivalent.
#
# The default is $myhostname + localhost.$mydomain + localhost. On
# a mail domain gateway, you should also include $mydomain.
#
# Do not specify the names of virtual domains - those domains are
# specified elsewhere (see VIRTUAL_README).
#
# Do not specify the names of domains that this machine is backup MX
# host for. Specify those names via the relay_domains settings for
# the SMTP server, or use permit_mx_backup if you are lazy (see
# STANDARD_CONFIGURATION_README).
#
# The local machine is always the final destination for mail addressed
# to user@[the.net.work.address] of an interface that the mail system
# receives mail on (see the inet_interfaces parameter).
#
# Specify a list of host or domain names, /file/name or type:table
# patterns, separated by commas and/or whitespace. A /file/name
# pattern is replaced by its contents; a type:table is matched when
# a name matches a lookup key (the right-hand side is ignored).
# Continue long lines by starting the next line with whitespace.
#
# See also below, section "REJECTING MAIL FOR UNKNOWN LOCAL USERS".
#
mydestination = $myhostname, localhost.$mydomain, localhost
#mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain
#mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain,
# mail.$mydomain, www.$mydomain, ftp.$mydomain
# REJECTING MAIL FOR UNKNOWN LOCAL USERS
#
# The local_recipient_maps parameter specifies optional lookup tables
# with all names or addresses of users that are local with respect
# to $mydestination, $inet_interfaces or $proxy_interfaces.
#
# If this parameter is defined, then the SMTP server will reject
# mail for unknown local users. This parameter is defined by default.
#
# To turn off local recipient checking in the SMTP server, specify
# local_recipient_maps = (i.e. empty).
#
# The default setting assumes that you use the default Postfix local
# delivery agent for local delivery. You need to update the
# local_recipient_maps setting if:
#
# - You define $mydestination domain recipients in files other than
# /etc/passwd, /etc/aliases, or the $virtual_alias_maps files.
# For example, you define $mydestination domain recipients in
# the $virtual_mailbox_maps files.
#
# - You redefine the local delivery agent in master.cf.
#
# - You redefine the "local_transport" setting in main.cf.
#
# - You use the "luser_relay", "mailbox_transport", or "fallback_transport"
# feature of the Postfix local delivery agent (see local(8)).
#
# Details are described in the LOCAL_RECIPIENT_README file.
#
# Beware: if the Postfix SMTP server runs chrooted, you probably have
# to access the passwd file via the proxymap service, in order to
# overcome chroot restrictions. The alternative, having a copy of
# the system passwd file in the chroot jail is just not practical.
#
# The right-hand side of the lookup tables is conveniently ignored.
# In the left-hand side, specify a bare username, an @domain.tld
# wild-card, or specify a user@domain.tld address.
#
#local_recipient_maps = unix:passwd.byname $alias_maps
#local_recipient_maps = proxy:unix:passwd.byname $alias_maps
#local_recipient_maps =
# The unknown_local_recipient_reject_code specifies the SMTP server
# response code when a recipient domain matches $mydestination or
# ${proxy,inet}_interfaces, while $local_recipient_maps is non-empty
# and the recipient address or address local-part is not found.
#
# The default setting is 550 (reject mail) but it is safer to start
# with 450 (try again later) until you are certain that your
# local_recipient_maps settings are OK.
#
unknown_local_recipient_reject_code = 550
# TRUST AND RELAY CONTROL
# The mynetworks parameter specifies the list of "trusted" SMTP
# clients that have more privileges than "strangers".
#
# In particular, "trusted" SMTP clients are allowed to relay mail
# through Postfix. See the smtpd_recipient_restrictions parameter
# in postconf(5).
#
# You can specify the list of "trusted" network addresses by hand
# or you can let Postfix do it for you (which is the default).
#
# By default (mynetworks_style = subnet), Postfix "trusts" SMTP
# clients in the same IP subnetworks as the local machine.
# On Linux, this does works correctly only with interfaces specified
# with the "ifconfig" command.
#
# Specify "mynetworks_style = class" when Postfix should "trust" SMTP
# clients in the same IP class A/B/C networks as the local machine.
# Don't do this with a dialup site - it would cause Postfix to "trust"
# your entire provider's network. Instead, specify an explicit
# mynetworks list by hand, as described below.
#
# Specify "mynetworks_style = host" when Postfix should "trust"
# only the local machine.
#
#mynetworks_style = class
#mynetworks_style = subnet
#mynetworks_style = host
# Alternatively, you can specify the mynetworks list by hand, in
# which case Postfix ignores the mynetworks_style setting.
#
# Specify an explicit list of network/netmask patterns, where the
# mask specifies the number of bits in the network part of a host
# address.
#
# You can also specify the absolute pathname of a pattern file instead
# of listing the patterns here. Specify type:table for table-based lookups
# (the value on the table right-hand side is not used).
#
#mynetworks = 168.100.189.0/28, 127.0.0.0/8
#mynetworks = $config_directory/mynetworks
#mynetworks = hash:/etc/postfix/network_table
mynetworks = 192.168.10.0/24,192.168.30.0/24,[2405:6580:27e0:1300::]/64,[::1],[FE80::]/10,[FEC0::]/10
# The relay_domains parameter restricts what destinations this system will
# relay mail to. See the smtpd_recipient_restrictions description in
# postconf(5) for detailed information.
#
# By default, Postfix relays mail
# - from "trusted" clients (IP address matches $mynetworks) to any destination,
# - from "untrusted" clients to destinations that match $relay_domains or
# subdomains thereof, except addresses with sender-specified routing.
# The default relay_domains value is $mydestination.
#
# In addition to the above, the Postfix SMTP server by default accepts mail
# that Postfix is final destination for:
# - destinations that match $inet_interfaces or $proxy_interfaces,
# - destinations that match $mydestination
# - destinations that match $virtual_alias_domains,
# - destinations that match $virtual_mailbox_domains.
# These destinations do not need to be listed in $relay_domains.
virtual_alias_domains = kamata-net.com, kamata-net.jp, mail.kamata-net.com
virtual_alias_maps = hash:/etc/postfix/virtual
# Specify a list of hosts or domains, /file/name patterns or type:name
# lookup tables, separated by commas and/or whitespace. Continue
# long lines by starting the next line with whitespace. A file name
# is replaced by its contents; a type:name table is matched when a
# (parent) domain appears as lookup key.
#
# NOTE: Postfix will not automatically forward mail for domains that
# list this system as their primary or backup MX host. See the
# permit_mx_backup restriction description in postconf(5).
#
relay_domains = $mydestination
# INTERNET OR INTRANET
# The relayhost parameter specifies the default host to send mail to
# when no entry is matched in the optional transport(5) table. When
# no relayhost is given, mail is routed directly to the destination.
#
# On an intranet, specify the organizational domain name. If your
# internal DNS uses no MX records, specify the name of the intranet
# gateway host instead.
#
# In the case of SMTP, specify a domain, host, host:port, [host]:port,
# [address] or [address]:port; the form [host] turns off MX lookups.
#
# If you're connected via UUCP, see also the default_transport parameter.
#
#relayhost = $mydomain
#relayhost = [gateway.my.domain]
#relayhost = [mailserver.isp.tld]
#relayhost = uucphost
#relayhost = [an.ip.add.ress]
#relayhost = [192.168.30.104]
# REJECTING UNKNOWN RELAY USERS
#
# The relay_recipient_maps parameter specifies optional lookup tables
# with all addresses in the domains that match $relay_domains.
#
# If this parameter is defined, then the SMTP server will reject
# mail for unknown relay users. This feature is off by default.
#
# The right-hand side of the lookup tables is conveniently ignored.
# In the left-hand side, specify an @domain.tld wild-card, or specify
# a user@domain.tld address.
#
#relay_recipient_maps = hash:/etc/postfix/relay_recipients
# INPUT RATE CONTROL
#
# The in_flow_delay configuration parameter implements mail input
# flow control. This feature is turned on by default, although it
# still needs further development (it's disabled on SCO UNIX due
# to an SCO bug).
#
# A Postfix process will pause for $in_flow_delay seconds before
# accepting a new message, when the message arrival rate exceeds the
# message delivery rate. With the default 100 SMTP server process
# limit, this limits the mail inflow to 100 messages a second more
# than the number of messages delivered per second.
#
# Specify 0 to disable the feature. Valid delays are 0..10.
#
#in_flow_delay = 1s
# ADDRESS REWRITING
#
# The ADDRESS_REWRITING_README document gives information about
# address masquerading or other forms of address rewriting including
# username->Firstname.Lastname mapping.
# ADDRESS REDIRECTION (VIRTUAL DOMAIN)
#
# The VIRTUAL_README document gives information about the many forms
# of domain hosting that Postfix supports.
# "USER HAS MOVED" BOUNCE MESSAGES
#
# See the discussion in the ADDRESS_REWRITING_README document.
# TRANSPORT MAP
#
# See the discussion in the ADDRESS_REWRITING_README document.
# ALIAS DATABASE
#
# The alias_maps parameter specifies the list of alias databases used
# by the local delivery agent. The default list is system dependent.
#
# On systems with NIS, the default is to search the local alias
# database, then the NIS alias database. See aliases(5) for syntax
# details.
#
# If you change the alias database, run "postalias /etc/aliases" (or
# wherever your system stores the mail alias file), or simply run
# "newaliases" to build the necessary DBM or DB file.
#
# It will take a minute or so before changes become visible. Use
# "postfix reload" to eliminate the delay.
#
#alias_maps = dbm:/etc/aliases
alias_maps = hash:/etc/aliases
#alias_maps = hash:/etc/aliases, nis:mail.aliases
#alias_maps = netinfo:/aliases
# The alias_database parameter specifies the alias database(s) that
# are built with "newaliases" or "sendmail -bi". This is a separate
# configuration parameter, because alias_maps (see above) may specify
# tables that are not necessarily all under control by Postfix.
#
#alias_database = dbm:/etc/aliases
#alias_database = dbm:/etc/mail/aliases
alias_database = hash:/etc/aliases
#alias_database = hash:/etc/aliases, hash:/opt/majordomo/aliases
# ADDRESS EXTENSIONS (e.g., user+foo)
#
# The recipient_delimiter parameter specifies the separator between
# user names and address extensions (user+foo). See canonical(5),
# local(8), relocated(5) and virtual(5) for the effects this has on
# aliases, canonical, virtual, relocated and .forward file lookups.
# Basically, the software tries user+foo and .forward+foo before
# trying user and .forward.
#
#recipient_delimiter = +
# DELIVERY TO MAILBOX
#
# The home_mailbox parameter specifies the optional pathname of a
# mailbox file relative to a user's home directory. The default
# mailbox file is /var/spool/mail/user or /var/mail/user. Specify
# "Maildir/" for qmail-style delivery (the / is required).
#
#home_mailbox = Mailbox
home_mailbox = Maildir/
# The mail_spool_directory parameter specifies the directory where
# UNIX-style mailboxes are kept. The default setting depends on the
# system type.
#
#mail_spool_directory = /var/mail
#mail_spool_directory = /var/spool/mail
# The mailbox_command parameter specifies the optional external
# command to use instead of mailbox delivery. The command is run as
# the recipient with proper HOME, SHELL and LOGNAME environment settings.
# Exception: delivery for root is done as $default_user.
#
# Other environment variables of interest: USER (recipient username),
# EXTENSION (address extension), DOMAIN (domain part of address),
# and LOCAL (the address localpart).
#
# Unlike other Postfix configuration parameters, the mailbox_command
# parameter is not subjected to $parameter substitutions. This is to
# make it easier to specify shell syntax (see example below).
#
# Avoid shell meta characters because they will force Postfix to run
# an expensive shell process. Procmail alone is expensive enough.
#
# IF YOU USE THIS TO DELIVER MAIL SYSTEM-WIDE, YOU MUST SET UP AN
# ALIAS THAT FORWARDS MAIL FOR ROOT TO A REAL USER.
#
#mailbox_command = /some/where/procmail
#mailbox_command = /some/where/procmail -a "$EXTENSION"
# The mailbox_transport specifies the optional transport in master.cf
# to use after processing aliases and .forward files. This parameter
# has precedence over the mailbox_command, fallback_transport and
# luser_relay parameters.
#
# Specify a string of the form transport:nexthop, where transport is
# the name of a mail delivery transport defined in master.cf. The
# :nexthop part is optional. For more details see the sample transport
# configuration file.
#
# NOTE: if you use this feature for accounts not in the UNIX password
# file, then you must update the "local_recipient_maps" setting in
# the main.cf file, otherwise the SMTP server will reject mail for
# non-UNIX accounts with "User unknown in local recipient table".
#
# Cyrus IMAP over LMTP. Specify ``lmtpunix cmd="lmtpd"
# listen="/var/imap/socket/lmtp" prefork=0'' in cyrus.conf.
#mailbox_transport = lmtp:unix:/var/lib/imap/socket/lmtp
# If using the cyrus-imapd IMAP server deliver local mail to the IMAP
# server using LMTP (Local Mail Transport Protocol), this is prefered
# over the older cyrus deliver program by setting the
# mailbox_transport as below:
#
# mailbox_transport = lmtp:unix:/var/lib/imap/socket/lmtp
#
# The efficiency of LMTP delivery for cyrus-imapd can be enhanced via
# these settings.
#
# local_destination_recipient_limit = 300
# local_destination_concurrency_limit = 5
#
# Of course you should adjust these settings as appropriate for the
# capacity of the hardware you are using. The recipient limit setting
# can be used to take advantage of the single instance message store
# capability of Cyrus. The concurrency limit can be used to control
# how many simultaneous LMTP sessions will be permitted to the Cyrus
# message store.
#
# Cyrus IMAP via command line. Uncomment the "cyrus...pipe" and
# subsequent line in master.cf.
#mailbox_transport = cyrus
# The fallback_transport specifies the optional transport in master.cf
# to use for recipients that are not found in the UNIX passwd database.
# This parameter has precedence over the luser_relay parameter.
#
# Specify a string of the form transport:nexthop, where transport is
# the name of a mail delivery transport defined in master.cf. The
# :nexthop part is optional. For more details see the sample transport
# configuration file.
#
# NOTE: if you use this feature for accounts not in the UNIX password
# file, then you must update the "local_recipient_maps" setting in
# the main.cf file, otherwise the SMTP server will reject mail for
# non-UNIX accounts with "User unknown in local recipient table".
#
#fallback_transport = lmtp:unix:/var/lib/imap/socket/lmtp
#fallback_transport =
# The luser_relay parameter specifies an optional destination address
# for unknown recipients. By default, mail for unknown@$mydestination,
# unknown@[$inet_interfaces] or unknown@[$proxy_interfaces] is returned
# as undeliverable.
#
# The following expansions are done on luser_relay: $user (recipient
# username), $shell (recipient shell), $home (recipient home directory),
# $recipient (full recipient address), $extension (recipient address
# extension), $domain (recipient domain), $local (entire recipient
# localpart), $recipient_delimiter. Specify ${name?value} or
# ${name:value} to expand value only when $name does (does not) exist.
#
# luser_relay works only for the default Postfix local delivery agent.
#
# NOTE: if you use this feature for accounts not in the UNIX password
# file, then you must specify "local_recipient_maps =" (i.e. empty) in
# the main.cf file, otherwise the SMTP server will reject mail for
# non-UNIX accounts with "User unknown in local recipient table".
#
#luser_relay = $user@other.host
#luser_relay = $local@other.host
#luser_relay = admin+$local
# JUNK MAIL CONTROLS
#
# The controls listed here are only a very small subset. The file
# SMTPD_ACCESS_README provides an overview.
# The header_checks parameter specifies an optional table with patterns
# that each logical message header is matched against, including
# headers that span multiple physical lines.
#
# By default, these patterns also apply to MIME headers and to the
# headers of attached messages. With older Postfix versions, MIME and
# attached message headers were treated as body text.
#
# For details, see "man header_checks".
#
#header_checks = regexp:/etc/postfix/header_checks
# FAST ETRN SERVICE
#
# Postfix maintains per-destination logfiles with information about
# deferred mail, so that mail can be flushed quickly with the SMTP
# "ETRN domain.tld" command, or by executing "sendmail -qRdomain.tld".
# See the ETRN_README document for a detailed description.
#
# The fast_flush_domains parameter controls what destinations are
# eligible for this service. By default, they are all domains that
# this server is willing to relay mail to.
#
#fast_flush_domains = $relay_domains
# SHOW SOFTWARE VERSION OR NOT
#
# The smtpd_banner parameter specifies the text that follows the 220
# code in the SMTP server's greeting banner. Some people like to see
# the mail version advertised. By default, Postfix shows no version.
#
# You MUST specify $myhostname at the start of the text. That is an
# RFC requirement. Postfix itself does not care.
#
#smtpd_banner = $myhostname ESMTP $mail_name
#smtpd_banner = $myhostname ESMTP $mail_name ($mail_version)
smtpd_banner = $myhostname ESMTP
# PARALLEL DELIVERY TO THE SAME DESTINATION
#
# How many parallel deliveries to the same user or domain? With local
# delivery, it does not make sense to do massively parallel delivery
# to the same user, because mailbox updates must happen sequentially,
# and expensive pipelines in .forward files can cause disasters when
# too many are run at the same time. With SMTP deliveries, 10
# simultaneous connections to the same domain could be sufficient to
# raise eyebrows.
#
# Each message delivery transport has its XXX_destination_concurrency_limit
# parameter. The default is $default_destination_concurrency_limit for
# most delivery transports. For the local delivery agent the default is 2.
#local_destination_concurrency_limit = 2
#default_destination_concurrency_limit = 20
# DEBUGGING CONTROL
#
# The debug_peer_level parameter specifies the increment in verbose
# logging level when an SMTP client or server host name or address
# matches a pattern in the debug_peer_list parameter.
#
debug_peer_level = 2
# The debug_peer_list parameter specifies an optional list of domain
# or network patterns, /file/name patterns or type:name tables. When
# an SMTP client or server host name or address matches a pattern,
# increase the verbose logging level by the amount specified in the
# debug_peer_level parameter.
#
#debug_peer_list = 127.0.0.1
#debug_peer_list = some.domain
#debug_peer_list = asahi-net.or.jp
# The debugger_command specifies the external command that is executed
# when a Postfix daemon program is run with the -D option.
#
# Use "command .. & sleep 5" so that the debugger can attach before
# the process marches on. If you use an X-based debugger, be sure to
# set up your XAUTHORITY environment variable before starting Postfix.
#
debugger_command =
PATH=/bin:/usr/bin:/usr/local/bin:/usr/X11R6/bin
ddd $daemon_directory/$process_name $process_id & sleep 5
# If you can't use X, use this to capture the call stack when a
# daemon crashes. The result is in a file in the configuration
# directory, and is named after the process name and the process ID.
#
# debugger_command =
# PATH=/bin:/usr/bin:/usr/local/bin; export PATH; (echo cont;
# echo where) | gdb $daemon_directory/$process_name $process_id 2>&1
# >$config_directory/$process_name.$process_id.log & sleep 5
#
# Another possibility is to run gdb under a detached screen session.
# To attach to the screen session, su root and run "screen -r
# <id_string>" where <id_string> uniquely matches one of the detached
# sessions (from "screen -list").
#
# debugger_command =
# PATH=/bin:/usr/bin:/sbin:/usr/sbin; export PATH; screen
# -dmS $process_name gdb $daemon_directory/$process_name
# $process_id & sleep 1
# INSTALL-TIME CONFIGURATION INFORMATION
#
# The following parameters are used when installing a new Postfix version.
#
# sendmail_path: The full pathname of the Postfix sendmail command.
# This is the Sendmail-compatible mail posting interface.
#
sendmail_path = /usr/sbin/sendmail.postfix
# newaliases_path: The full pathname of the Postfix newaliases command.
# This is the Sendmail-compatible command to build alias databases.
#
newaliases_path = /usr/bin/newaliases.postfix
# mailq_path: The full pathname of the Postfix mailq command. This
# is the Sendmail-compatible mail queue listing command.
#
mailq_path = /usr/bin/mailq.postfix
# setgid_group: The group for mail submission and queue management
# commands. This must be a group name with a numerical group ID that
# is not shared with other accounts, not even with the Postfix account.
#
setgid_group = postdrop
# html_directory: The location of the Postfix HTML documentation.
#
html_directory = no
# manpage_directory: The location of the Postfix on-line manual pages.
#
manpage_directory = /usr/share/man
# sample_directory: The location of the Postfix sample configuration files.
# This parameter is obsolete as of Postfix 2.1.
#
sample_directory = /usr/share/doc/postfix/samples
# readme_directory: The location of the Postfix README files.
#
readme_directory = /usr/share/doc/postfix/README_FILES
# TLS CONFIGURATION
#
# Basic Postfix TLS configuration by default with self-signed certificate
# for inbound SMTP and also opportunistic TLS for outbound SMTP.
# The full pathname of a file with the Postfix SMTP server RSA certificate
# in PEM format. Intermediate certificates should be included in general,
# the server certificate first, then the issuing CA(s) (bottom-up order).
#
smtpd_tls_cert_file = /etc/pki/postfix/certs/postfix.pem
# The full pathname of a file with the Postfix SMTP server RSA private key
# in PEM format. The private key must be accessible without a pass-phrase,
# i.e. it must not be encrypted.
#
smtpd_tls_key_file = /etc/pki/postfix/private/privkey.pem
# Announce STARTTLS support to remote SMTP clients, but do not require that
# clients use TLS encryption (opportunistic TLS inbound).
#
smtpd_tls_security_level = may
# Directory with PEM format Certification Authority certificates that the
# Postfix SMTP client uses to verify a remote SMTP server certificate.
#
smtp_tls_CApath = /etc/pki/postfix/certs
# The full pathname of a file containing CA certificates of root CAs
# trusted to sign either remote SMTP server certificates or intermediate CA
# certificates.
#
#smtp_tls_CAfile = /etc/pki/postfix/certs/ca-bundle.crt
smtp_tls_CAfile = /etc/pki/postfix/cacert.pem
# Use TLS if this is supported by the remote SMTP server, otherwise use
# plaintext (opportunistic TLS outbound).
#
meta_directory = /etc/postfix
shlib_directory = /usr/lib64/postfix
transport_maps = hash:/etc/postfix/transport
content_filter = smtp-amavis:[127.0.0.1]:10024
# VRFYコマンド無効化
disable_vrfy_command = yes
# HELOコマンドを要求する(スパム対策)
smtpd_helo_required = yes
# MAIL FROMやRCPT TOコマンドに不正な文法を認めない
strict_rfc821_envelopes = yes
# SMTP DATA コマンドの場面で適用するオプションの制限
smtpd_data_restrictions =
reject_unauth_pipelining,
reject_multi_recipient_bounce
# SMTP HELO コマンドの場面で適用するオプションの制限
smtpd_helo_restrictions =
permit_mynetworks,
reject_invalid_hostname,
reject_non_fqdn_hostname,
reject_unknown_hostname,
permit
# MAIL FROM コマンドの場面で適用するオプションの制限
smtpd_sender_restrictions =
permit_mynetworks,
reject_unknown_sender_domain,
reject_non_fqdn_sender,
permit
# ETRN 要求の場面で適用するオプションの制限
smtpd_etrn_restrictions =
permit_mynetworks,
reject_invalid_hostname,
permit
# SMTP-Auth
# SASL認証有効化
#自身のSMTP-AUTH化
smtpd_sasl_auth_enable = yes
#接続先(Submission用)のSMTP-AUTH
smtp_sasl_auth_enable = yes
# mynetworks以外で匿名での接続を拒否
smtpd_sasl_security_options = noanonymous
smtp_sasl_security_options = noanonymous
# 規格外の動作に対応
broken_sasl_auth_clients = yes
#SMTP-Auth User:Password
smtp_sasl_password_maps = hash:/etc/postfix/relay_password
# RCPT TO コマンドの場面で適用するアクセス制限。SMTP_Authを利用したクラアントを許可
smtpd_recipient_restrictions =
permit_mynetworks
permit_sasl_authenticated
reject_unauth_destination
check_policy_service unix:private/policy-spf
# DKIM署名
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = inet:localhost:8891
milter_default_action = accept
master.cf
#
# Postfix master process configuration file. For details on the format
# of the file, see the master(5) manual page (command: "man 5 master" or
# on-line: http://www.postfix.org/master.5.html).
#
# Do not forget to execute "postfix reload" after editing this file.
#
# ==========================================================================
# service type private unpriv chroot wakeup maxproc command + args
# (yes) (yes) (no) (never) (100)
# ==========================================================================
smtp inet n - n - - smtpd
#smtp inet n - n - 1 postscreen
#smtpd pass - - n - - smtpd
#dnsblog unix - - n - 0 dnsblog
#tlsproxy unix - - n - 0 tlsproxy
#submission inet n - n - - smtpd
# -o syslog_name=postfix/submission
# -o smtpd_tls_security_level=encrypt
# -o smtpd_sasl_auth_enable=yes
# -o smtpd_tls_auth_only=yes
# -o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
# -o smtpd_recipient_restrictions=
# -o smtpd_relay_restrictions=permit_sasl_authenticated,reject
# -o milter_macro_daemon_name=ORIGINATING
#smtps inet n - n - - smtpd
# -o syslog_name=postfix/smtps
# -o smtpd_tls_wrappermode=yes
# -o smtpd_sasl_auth_enable=yes
# -o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
# -o smtpd_recipient_restrictions=
# -o smtpd_relay_restrictions=permit_sasl_authenticated,reject
# -o milter_macro_daemon_name=ORIGINATING
#628 inet n - n - - qmqpd
pickup unix n - n 60 1 pickup
cleanup unix n - n - 0 cleanup
qmgr unix n - n 300 1 qmgr
#qmgr unix n - n 300 1 oqmgr
tlsmgr unix - - n 1000? 1 tlsmgr
rewrite unix - - n - - trivial-rewrite
bounce unix - - n - 0 bounce
defer unix - - n - 0 bounce
trace unix - - n - 0 bounce
verify unix - - n - 1 verify
flush unix n - n 1000? 0 flush
proxymap unix - - n - - proxymap
proxywrite unix - - n - 1 proxymap
smtp unix - - n - - smtp
relay unix - - n - - smtp
-o syslog_name=postfix/$service_name
# -o smtp_helo_timeout=5 -o smtp_connect_timeout=5
showq unix n - n - - showq
error unix - - n - - error
retry unix - - n - - error
discard unix - - n - - discard
local unix - n n - - local
virtual unix - n n - - virtual
lmtp unix - - n - - lmtp
anvil unix - - n - 1 anvil
scache unix - - n - 1 scache
#
# ====================================================================
# Interfaces to non-Postfix software. Be sure to examine the manual
# pages of the non-Postfix software to find out what options it wants.
#
# Many of the following services use the Postfix pipe(8) delivery
# agent. See the pipe(8) man page for information about ${recipient}
# and other message envelope options.
# ====================================================================
#
# maildrop. See the Postfix MAILDROP_README file for details.
# Also specify in main.cf: maildrop_destination_recipient_limit=1
#
#maildrop unix - n n - - pipe
# flags=DRhu user=vmail argv=/usr/local/bin/maildrop -d ${recipient}
#
# ====================================================================
#
# Recent Cyrus versions can use the existing "lmtp" master.cf entry.
#
# Specify in cyrus.conf:
# lmtp cmd="lmtpd -a" listen="localhost:lmtp" proto=tcp4
#
# Specify in main.cf one or more of the following:
# mailbox_transport = lmtp:inet:localhost
# virtual_transport = lmtp:inet:localhost
#
# ====================================================================
#
# Cyrus 2.1.5 (Amos Gouaux)
# Also specify in main.cf: cyrus_destination_recipient_limit=1
#
#cyrus unix - n n - - pipe
# user=cyrus argv=/usr/lib/cyrus-imapd/deliver -e -r ${sender} -m ${extension} ${user}
#
# ====================================================================
#
# Old example of delivery via Cyrus.
#
#old-cyrus unix - n n - - pipe
# flags=R user=cyrus argv=/usr/lib/cyrus-imapd/deliver -e -m ${extension} ${user}
#
# ====================================================================
#
# See the Postfix UUCP_README file for configuration details.
#
#uucp unix - n n - - pipe
# flags=Fqhu user=uucp argv=uux -r -n -z -a$sender - $nexthop!rmail ($recipient)
#
# ====================================================================
#
# Other external delivery methods.
#
#ifmail unix - n n - - pipe
# flags=F user=ftn argv=/usr/lib/ifmail/ifmail -r $nexthop ($recipient)
#
#bsmtp unix - n n - - pipe
# flags=Fq. user=bsmtp argv=/usr/local/sbin/bsmtp -f $sender $nexthop $recipient
#
#scalemail-backend unix - n n - 2 pipe
# flags=R user=scalemail argv=/usr/lib/scalemail/bin/scalemail-store
# ${nexthop} ${user} ${extension}
#
#mailman unix - n n - - pipe
# flags=FR user=list argv=/usr/lib/mailman/bin/postfix-to-mailman.py
# ${nexthop} ${user}
policy-spf unix - n n - 0 spawn user=nobody argv=/usr/bin/python3 /usr/libexec/postfix/policyd-spf /etc/python-policyd-spf/policyd-spf.conf
#spamassassin unix - n n - - pipe flags=R user=spamd argv=/usr/bin/spamc -e /usr/sbin/sendmail -oi -f ${sender} ${recipient}
smtp-amavis unix - - n - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
127.0.0.1:10025 inet n - n - - smtpd
-o content_filter=
-o local_recipient_maps=
-o relay_recipient_maps=
-o smtpd_restriction_classes=
-o smtpd_delay_reject=no
-o smtpd_client_restrictions=permit_mynetworks,reject
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o mynetworks_style=host
-o mynetworks=127.0.0.0/8
-o strict_rfc821_envelopes=yes
-o smtpd_error_sleep_time=0
-o smtpd_soft_error_limit=1001
-o smtpd_hard_error_limit=1000
-o smtpd_client_connection_count_limit=0
-o smtpd_client_connection_rate_limit=0
-o receive_override_options=no_header_body_checks,no_unknown_recipient_checks
# -o content_filter=
# -o local_recipient_maps=
# -o relay_recipient_maps=
# -o smtpd_restriction_classes=
# -o smtpd_client_restrictions=
# -o smtpd_helo_restrictions=
# -o smtpd_sender_restrictions=
# -o smtpd_recipient_restrictions=permit_mynetworks,reject
# -o mynetworks=127.0.0.0/8
# -o strict_rfc821_envelopes=yes
# -o smtpd_error_sleep_time=0
# -o smtpd_soft_error_limit=1001
# -o smtpd_hard_error_limit=1000
smtps inet n - n - - smtpd
# -o syslog_name=postfix/smtps
-o smtpd_tls_wrappermode=yes
-o smtpd_sasl_auth_enable=yes
# -o smtpd_reject_unlisted_recipient=no
# -o smtpd_client_restrictions=$mua_client_restrictions
# -o smtpd_helo_restrictions=$mua_helo_restrictions
# -o smtpd_sender_restrictions=$mua_sender_restrictions
-o smtpd_recipient_restrictions=permit_sasl_authenticated,reject
# -o milter_macro_daemon_name=ORIGINATING
virtual
# VIRTUAL(5) VIRTUAL(5)
#
# NAME
# virtual - Postfix virtual alias table format
#
〜〜
#
# AUTHOR(S)
# Wietse Venema
# IBM T.J. Watson Research
# P.O. Box 704
# Yorktown Heights, NY 10598, USA
#
# Wietse Venema
# Google, Inc.
# 111 8th Avenue
# New York, NY 10011, USA
#
# VIRTUAL(5)
mailaccount@kamata-net.com mailaccount@(内部メールサーバー名).kamata-net.com ★ 内部メールサーバーへ転送したい
mailaccount2@kamata-net.com localaccount mailaccount2@(内部メールサーバ名).kamata-net.com ★内部メールサーバーへ転送するとともにローカル配送もしたい(iPhoneで読みたい)
localaccount@mail.kamata-net.com localacount ★ ローカル配送のみ
# Catch-all
@kamata-net.com @(内部メールサーバー名).kamata-net.com ★その他のメールはすべて内部メールサーバーへ転送
#
postmaster@kamata-net.jp postmaster@(内部メールサーバー名).kamata-net.com
#
webmaster@kamata-net.jp webmaster@(内部メールサーバー名).kamata-net.com
transport
# TRANSPORT(5) TRANSPORT(5)
#
# NAME
# transport - Postfix transport table format
#
〜〜
# AUTHOR(S)
# Wietse Venema
# IBM T.J. Watson Research
# P.O. Box 704
# Yorktown Heights, NY 10598, USA
#
# Wietse Venema
# Google, Inc.
# 111 8th Avenue
# New York, NY 10011, USA
#
# TRANSPORT(5)
localhost : ★ローカル配送指定
localhost.localdomain : ★ローカル配送指定
mail.kamata-net.com : ★ローカル配送指定
yahoo.co.jp smtp: ★yahooは直接配送
(内部メールサーバー).kamata-net.com smtp:[192.168.30.xxx]:25 ★内部向けのルート設定
* smtp:[mail.asahi-net.or.jp]:587 ★ 上記以外はすべてAsahi-netへ
Amavisd-New
amavisd.conf
use strict;
# a minimalistic configuration file for amavisd-new with all necessary settings
#
# see amavisd.conf-default for a list of all variables with their defaults;
# for more details see documentation in INSTALL, README_FILES/*
# and at http://www.ijs.si/software/amavisd/amavisd-new-docs.html
# COMMONLY ADJUSTED SETTINGS:
#@bypass_virus_checks_maps = (1); # controls running of anti-virus code
#@bypass_spam_checks_maps = (1); # controls running of anti-spam code
# $bypass_decode_parts = 1; # controls running of decoders&dearchivers
# $myprogram_name = $0; # set to 'amavisd' or similar to avoid process name
# truncation in /proc/<pid>/stat and ps -e output
$max_servers = 2; # num of pre-forked children (2..30 is common), -m
$daemon_user = 'amavis'; # (no default; customary: vscan or amavis), -u
$daemon_group = 'amavis'; # (no default; customary: vscan or amavis), -g
$mydomain = 'mailexchange.jp'; # a convenient default for other settings
$MYHOME = '/var/spool/amavisd'; # a convenient default for other settings, -H
$TEMPBASE = "$MYHOME/tmp"; # working directory, needs to exist, -T
$ENV{TMPDIR} = $TEMPBASE; # environment variable TMPDIR, used by SA, etc.
$QUARANTINEDIR = undef; # -Q
# $quarantine_subdir_levels = 1; # add level of subdirs to disperse quarantine
# $release_format = 'resend'; # 'attach', 'plain', 'resend'
# $report_format = 'arf'; # 'attach', 'plain', 'resend', 'arf'
# $daemon_chroot_dir = $MYHOME; # chroot directory or undef, -R
$db_home = "$MYHOME/db"; # dir for bdb nanny/cache/snmp databases, -D
# $helpers_home = "$MYHOME/var"; # working directory for SpamAssassin, -S
$lock_file = "/run/amavisd/amavisd.lock"; # -L
$pid_file = "/run/amavisd/amavisd.pid"; # -P
#NOTE: create directories $MYHOME/tmp, $MYHOME/var, $MYHOME/db manually
$log_level = 0; # verbosity 0..5, -d
$log_recip_templ = undef; # disable by-recipient level-0 log entries
$do_syslog = 1; # log via syslogd (preferred)
$syslog_facility = 'mail'; # Syslog facility as a string
# e.g.: mail, daemon, user, local0, ... local7
$enable_db = 1; # enable use of BerkeleyDB/libdb (SNMP and nanny)
# $enable_zmq = 1; # enable use of ZeroMQ (SNMP and nanny)
$nanny_details_level = 2; # nanny verbosity: 1: traditional, 2: detailed
$enable_dkim_verification = 0; # enable DKIM signatures verification
$enable_dkim_signing = 0; # load DKIM signing code, keys defined by dkim_key
#@local_domains_maps = ( [".$mydomain","hne.jp","kamata-net.com","kamata-net.jp","nishimine.net","mailexchange.jp"] ); # list of all local domains
@local_domains_maps = (1);
@mynetworks = qw( 127.0.0.0/8 [::1] [FE80::]/10 [FEC0::]/10 [2405:6580:27e0:1300::]/64
10.0.0.0/8 172.16.0.0/12 192.168.10.0/24 192.168.30.0/24 );
$unix_socketname = "/run/amavisd/amavisd.sock"; # amavisd-release or amavis-milter
# option(s) -p overrides $inet_socket_port and $unix_socketname
# The default receiving port in the Fedora and RHEL SELinux policy is 10024.
# To allow additional ports you need to label them as 'amavisd_recv_port_t'
# For example: semanage port -a -t amavisd_recv_port_t -p tcp 10022
$inet_socket_port = 10024; # listen on this local TCP port(s)
# $inet_socket_port = [10022,10024]; # listen on multiple TCP ports
$policy_bank{'MYNETS'} = { # mail originating from @mynetworks
originating => 1, # is true in MYNETS by default, but let's make it explicit
os_fingerprint_method => undef, # don't query p0f for internal clients
};
# it is up to MTA to re-route mail from authenticated roaming users or
# from internal hosts to a dedicated TCP port (such as 10022) for filtering
$interface_policy{'10022'} = 'ORIGINATING';
$policy_bank{'ORIGINATING'} = { # mail supposedly originating from our users
originating => 1, # declare that mail was submitted by our smtp client
allow_disclaimers => 1, # enables disclaimer insertion if available
# notify administrator of locally originating malware
virus_admin_maps => ["virusalert\@$mydomain"],
spam_admin_maps => ["virusalert\@$mydomain"],
warnbadhsender => 1,
# forward to a smtpd service providing DKIM signing service
forward_method => 'smtp:[127.0.0.1]:10025',
# force MTA conversion to 7-bit (e.g. before DKIM signing)
smtpd_discard_ehlo_keywords => ['8BITMIME'],
bypass_banned_checks_maps => [1], # allow sending any file names and types
terminate_dsn_on_notify_success => 0, # don't remove NOTIFY=SUCCESS option
};
$interface_policy{'SOCK'} = 'AM.PDP-SOCK'; # only applies with $unix_socketname
# Use with amavis-release over a socket or with Petr Rehor's amavis-milter.c
# (with amavis-milter.c from this package or old amavis.c client use 'AM.CL'):
$policy_bank{'AM.PDP-SOCK'} = {
protocol => 'AM.PDP',
auth_required_release => 0, # do not require secret_id for amavisd-release
};
#$sa_tag_level_deflt = 2.0; # add spam info headers if at, or above that level
$sa_tag_level_deflt = -999; # add spam info headers if at, or above that level
$sa_tag2_level_deflt = 6.2; # add 'spam detected' headers at that level
$sa_kill_level_deflt = 6.9; # triggers spam evasive actions (e.g. blocks mail)
$sa_dsn_cutoff_level = 10; # spam level beyond which a DSN is suppressed
$sa_crediblefrom_dsn_cutoff_level = 18; # likewise, but for a likely valid From
# $sa_quarantine_cutoff_level = 25; # spam level beyond which quarantine is off
$penpals_bonus_score = 8; # (no effect without a @storage_sql_dsn database)
$penpals_threshold_high = $sa_kill_level_deflt; # don't waste time on hi spam
$bounce_killer_score = 100; # spam score points to add for joe-jobbed bounces
$sa_mail_body_size_limit = 400*1024; # don't waste time on SA if mail is larger
$sa_local_tests_only = 0; # only tests which do not require internet access?
# @lookup_sql_dsn =
# ( ['DBI:mysql:database=mail;host=127.0.0.1;port=3306', 'user1', 'passwd1'],
# ['DBI:mysql:database=mail;host=host2', 'username2', 'password2'],
# ["DBI:SQLite:dbname=$MYHOME/sql/mail_prefs.sqlite", '', ''] );
# @storage_sql_dsn = @lookup_sql_dsn; # none, same, or separate database
# @storage_redis_dsn = ( {server=>'127.0.0.1:6379', db_id=>1} );
# $redis_logging_key = 'amavis-log';
# $redis_logging_queue_size_limit = 300000; # about 250 MB / 100000
# $timestamp_fmt_mysql = 1; # if using MySQL *and* msgs.time_iso is TIMESTAMP;
# defaults to 0, which is good for non-MySQL or if msgs.time_iso is CHAR(16)
#$virus_admin = undef; # notifications recip.
$mailfrom_notify_admin = undef; # notifications sender
$mailfrom_notify_recip = undef; # notifications sender
$mailfrom_notify_spamadmin = undef; # notifications sender
$mailfrom_to_quarantine = ''; # null return path; uses original sender if undef
@addr_extension_virus_maps = ('virus');
@addr_extension_banned_maps = ('banned');
@addr_extension_spam_maps = ('spam');
@addr_extension_bad_header_maps = ('badh');
# $recipient_delimiter = '+'; # undef disables address extensions altogether
# when enabling addr extensions do also Postfix/main.cf: recipient_delimiter=+
$path = '/usr/local/sbin:/usr/local/bin:/usr/sbin:/sbin:/usr/bin:/bin';
# $dspam = 'dspam';
$MAXLEVELS = 14;
$MAXFILES = 3000;
$MIN_EXPANSION_QUOTA = 100*1024; # bytes (default undef, not enforced)
$MAX_EXPANSION_QUOTA = 500*1024*1024; # bytes (default undef, not enforced)
$sa_spam_subject_tag = '***Spam*** ';
$defang_virus = 1; # MIME-wrap passed infected mail
$defang_banned = 1; # MIME-wrap passed mail containing banned name
# for defanging bad headers only turn on certain minor contents categories:
$defang_by_ccat{CC_BADH.",3"} = 1; # NUL or CR character in header
$defang_by_ccat{CC_BADH.",5"} = 1; # header line longer than 998 characters
$defang_by_ccat{CC_BADH.",6"} = 1; # header field syntax error
# OTHER MORE COMMON SETTINGS (defaults may suffice):
# $myhostname = 'host.example.com'; # must be a fully-qualified domain name!
$myhostname = 'smtp.mailexchange.jp'; # must be a fully-qualified domain name!
# The default forwarding port in the Fedora and RHEL SELinux policy is 10025.
# To allow additional ports you need to label them as 'amavisd_send_port_t'.
# For example: semanage port -a -t amavisd_send_port_t -p tcp 10023
# $notify_method = 'smtp:[127.0.0.1]:10023';
# $forward_method = 'smtp:[127.0.0.1]:10023'; # set to undef with milter!
$final_virus_destiny = D_DISCARD;
$final_banned_destiny = D_BOUNCE;
$final_spam_destiny = D_DISCARD; #!!! D_DISCARD / D_REJECT
$final_bad_header_destiny = D_BOUNCE;
# $bad_header_quarantine_method = undef;
# $os_fingerprint_method = 'p0f:*:2345'; # to query p0f-analyzer.pl
## hierarchy by which a final setting is chosen:
## policy bank (based on port or IP address) -> *_by_ccat
## *_by_ccat (based on mail contents) -> *_maps
## *_maps (based on recipient address) -> final configuration value
# SOME OTHER VARIABLES WORTH CONSIDERING (see amavisd.conf-default for all)
# $warnbadhsender,
# $warnvirusrecip, $warnbannedrecip, $warnbadhrecip, (or @warn*recip_maps)
#
# @bypass_virus_checks_maps, @bypass_spam_checks_maps,
# @bypass_banned_checks_maps, @bypass_header_checks_maps,
#
# @virus_lovers_maps, @spam_lovers_maps,
# @banned_files_lovers_maps, @bad_header_lovers_maps,
#
# @blacklist_sender_maps, @score_sender_maps,
#
# $clean_quarantine_method, $virus_quarantine_to, $banned_quarantine_to,
# $bad_header_quarantine_to, $spam_quarantine_to,
#
# $defang_bad_header, $defang_undecipherable, $defang_spam
# REMAINING IMPORTANT VARIABLES ARE LISTED HERE BECAUSE OF LONGER ASSIGNMENTS
@keep_decoded_original_maps = (new_RE(
qr'^MAIL$', # let virus scanner see full original message
qr'^MAIL-UNDECIPHERABLE$', # same as ^MAIL$ if mail is undecipherable
qr'^(ASCII(?! cpio)|text|uuencoded|xxencoded|binhex)'i,
# qr'^Zip archive data', # don't trust Archive::Zip
));
$banned_filename_re = new_RE(
### BLOCKED ANYWHERE
# qr'^UNDECIPHERABLE$', # is or contains any undecipherable components
# qr'^\.(exe-ms|dll)$', # banned file(1) types, rudimentary
# qr'^\.(exe|lha|cab|dll)$', # banned file(1) types
### BLOCK THE FOLLOWING, EXCEPT WITHIN UNIX ARCHIVES:
# [ qr'^\.(gz|bz2)$' => 0 ], # allow any in gzip or bzip2
[ qr'^\.(rpm|cpio|tar)$' => 0 ], # allow any in Unix-type archives
qr'.\.(pif|scr)$'i, # banned extensions - rudimentary
# qr'^\.zip$', # block zip type
### BLOCK THE FOLLOWING, EXCEPT WITHIN ARCHIVES:
# [ qr'^\.(zip|rar|arc|arj|zoo)$'=> 0 ], # allow any within these archives
qr'^application/x-msdownload$'i, # block these MIME types
qr'^application/x-msdos-program$'i,
qr'^application/hta$'i,
# qr'^message/partial$'i, # rfc2046 MIME type
# qr'^message/external-body$'i, # rfc2046 MIME type
# qr'^(application/x-msmetafile|image/x-wmf)$'i, # Windows Metafile MIME type
# qr'^\.wmf$', # Windows Metafile file(1) type
# block certain double extensions in filenames
qr'^(?!cid:).*\.[^./]*[A-Za-z][^./]*\.\s*(exe|vbs|pif|scr|bat|cmd|com|cpl|dll)[.\s]*$'i,
# qr'\{[0-9a-f]{8}(-[0-9a-f]{4}){3}-[0-9a-f]{12}\}?'i, # Class ID CLSID, strict
# qr'\{[0-9a-z]{4,}(-[0-9a-z]{4,}){0,7}\}?'i, # Class ID extension CLSID, loose
qr'.\.(exe|vbs|pif|scr|cpl)$'i, # banned extension - basic
# qr'.\.(exe|vbs|pif|scr|cpl|bat|cmd|com)$'i, # banned extension - basic+cmd
# qr'.\.(ade|adp|app|bas|bat|chm|cmd|com|cpl|crt|emf|exe|fxp|grp|hlp|hta|
# inf|ini|ins|isp|js|jse|lib|lnk|mda|mdb|mde|mdt|mdw|mdz|msc|msi|
# msp|mst|ocx|ops|pcd|pif|prg|reg|scr|sct|shb|shs|sys|vb|vbe|vbs|vxd|
# wmf|wsc|wsf|wsh)$'ix, # banned extensions - long
# qr'.\.(asd|asf|asx|url|vcs|wmd|wmz)$'i, # consider also
# qr'.\.(ani|cur|ico)$'i, # banned cursors and icons filename
# qr'^\.ani$', # banned animated cursor file(1) type
# qr'.\.(mim|b64|bhx|hqx|xxe|uu|uue)$'i, # banned extension - WinZip vulnerab.
);
# See http://support.microsoft.com/default.aspx?scid=kb;EN-US;q262631
# and http://www.cknow.com/vtutor/vtextensions.htm
# ENVELOPE SENDER SOFT-WHITELISTING / SOFT-BLACKLISTING
@score_sender_maps = ({ # a by-recipient hash lookup table,
# results from all matching recipient tables are summed
# ## per-recipient personal tables (NOTE: positive: black, negative: white)
# 'user1@example.com' => [{'bla-mobile.press@example.com' => 10.0}],
# 'user3@example.com' => [{'.ebay.com' => -3.0}],
# 'user4@example.com' => [{'cleargreen@cleargreen.com' => -7.0,
# '.cleargreen.com' => -5.0}],
## site-wide opinions about senders (the '.' matches any recipient)
'.' => [ # the _first_ matching sender determines the score boost
new_RE( # regexp-type lookup table, just happens to be all soft-blacklist
[qr'^(bulkmail|offers|cheapbenefits|earnmoney|foryou)@'i => 5.0],
[qr'^(greatcasino|investments|lose_weight_today|market\.alert)@'i=> 5.0],
[qr'^(money2you|MyGreenCard|new\.tld\.registry|opt-out|opt-in)@'i=> 5.0],
[qr'^(optin|saveonlsmoking2002k|specialoffer|specialoffers)@'i => 5.0],
[qr'^(stockalert|stopsnoring|wantsome|workathome|yesitsfree)@'i => 5.0],
[qr'^(your_friend|greatoffers)@'i => 5.0],
[qr'^(inkjetplanet|marketopt|MakeMoney)\d*@'i => 5.0],
),
# read_hash("/var/amavis/sender_scores_sitewide"),
{ # a hash-type lookup table (associative array)
'nobody@cert.org' => -3.0,
'cert-advisory@us-cert.gov' => -3.0,
'owner-alert@iss.net' => -3.0,
'slashdot@slashdot.org' => -3.0,
'securityfocus.com' => -3.0,
'ntbugtraq@listserv.ntbugtraq.com' => -3.0,
'security-alerts@linuxsecurity.com' => -3.0,
'mailman-announce-admin@python.org' => -3.0,
'amavis-user-admin@lists.sourceforge.net'=> -3.0,
'amavis-user-bounces@lists.sourceforge.net' => -3.0,
'spamassassin.apache.org' => -3.0,
'notification-return@lists.sophos.com' => -3.0,
'owner-postfix-users@postfix.org' => -3.0,
'owner-postfix-announce@postfix.org' => -3.0,
'owner-sendmail-announce@lists.sendmail.org' => -3.0,
'sendmail-announce-request@lists.sendmail.org' => -3.0,
'donotreply@sendmail.org' => -3.0,
'ca+envelope@sendmail.org' => -3.0,
'noreply@freshmeat.net' => -3.0,
'owner-technews@postel.acm.org' => -3.0,
'ietf-123-owner@loki.ietf.org' => -3.0,
'cvs-commits-list-admin@gnome.org' => -3.0,
'rt-users-admin@lists.fsck.com' => -3.0,
'clp-request@comp.nus.edu.sg' => -3.0,
'surveys-errors@lists.nua.ie' => -3.0,
'emailnews@genomeweb.com' => -5.0,
'yahoo-dev-null@yahoo-inc.com' => -3.0,
'returns.groups.yahoo.com' => -3.0,
'clusternews@linuxnetworx.com' => -3.0,
lc('lvs-users-admin@LinuxVirtualServer.org') => -3.0,
lc('owner-textbreakingnews@CNNIMAIL12.CNN.COM') => -5.0,
# soft-blacklisting (positive score)
'sender@example.net' => 3.0,
'.example.net' => 1.0,
},
], # end of site-wide tables
});
@decoders = (
['mail', \&do_mime_decode],
# [[qw(asc uue hqx ync)], \&do_ascii], # not safe
['F', \&do_uncompress, ['unfreeze', 'freeze -d', 'melt', 'fcat'] ],
['Z', \&do_uncompress, ['uncompress', 'gzip -d', 'zcat'] ],
['gz', \&do_uncompress, 'gzip -d'],
['gz', \&do_gunzip],
['bz2', \&do_uncompress, 'bzip2 -d'],
['xz', \&do_uncompress,
['xzdec', 'xz -dc', 'unxz -c', 'xzcat'] ],
['lzma', \&do_uncompress,
['lzmadec', 'xz -dc --format=lzma',
'lzma -dc', 'unlzma -c', 'lzcat', 'lzmadec'] ],
# ['lrz', \&do_uncompress,
# ['lrzip -q -k -d -o -', 'lrzcat -q -k'] ],
['lzo', \&do_uncompress, 'lzop -d'],
['lz4', \&do_uncompress, ['lz4c -d'] ],
['rpm', \&do_uncompress, ['rpm2cpio.pl', 'rpm2cpio'] ],
[['cpio','tar'], \&do_pax_cpio, ['pax', 'gcpio', 'cpio'] ],
# ['/usr/local/heirloom/usr/5bin/pax', 'pax', 'gcpio', 'cpio']
['deb', \&do_ar, 'ar'],
# ['a', \&do_ar, 'ar'], # unpacking .a seems an overkill
['rar', \&do_unrar, ['unrar', 'rar'] ],
['arj', \&do_unarj, ['unarj', 'arj'] ],
['arc', \&do_arc, ['nomarch', 'arc'] ],
['zoo', \&do_zoo, ['zoo', 'unzoo'] ],
# ['doc', \&do_ole, 'ripole'], # no ripole package so far
['cab', \&do_cabextract, 'cabextract'],
# ['tnef', \&do_tnef_ext, 'tnef'], # use internal do_tnef() instead
['tnef', \&do_tnef],
# ['lha', \&do_lha, 'lha'], # not safe, use 7z instead
# ['sit', \&do_unstuff, 'unstuff'], # not safe
[['zip','kmz'], \&do_7zip, ['7za', '7z'] ],
[['zip','kmz'], \&do_unzip],
['7z', \&do_7zip, ['7zr', '7za', '7z'] ],
[[qw(gz bz2 Z tar)],
\&do_7zip, ['7za', '7z'] ],
[[qw(xz lzma jar cpio arj rar swf lha iso cab deb rpm)],
\&do_7zip, '7z' ],
['exe', \&do_executable, ['unrar','rar'], 'lha', ['unarj','arj'] ],
);
@av_scanners = (
# ### http://www.sophos.com/
# ['Sophos-SSSP', # SAV Dynamic Interface
# \&ask_daemon, ["{}", 'sssp:/run/savdi/sssp.sock'],
# # or: ["{}", 'sssp:[127.0.0.1]:4010'],
# qr/^DONE OK\b/m, qr/^VIRUS\b/m, qr/^VIRUS\s*(\S*)/m ],
# ### http://www.clanfield.info/sophie/ (http://www.vanja.com/tools/sophie/)
# ['Sophie',
# \&ask_daemon, ["{}/\n", 'sophie:/run/sophie'],
# qr/(?x)^ 0+ ( : | [\000\r\n]* $)/, qr/(?x)^ 1 ( : | [\000\r\n]* $)/,
# qr/(?x)^ [-+]? \d+ : (.*?) [\000\r\n]* $/m ],
# ### http://www.csupomona.edu/~henson/www/projects/SAVI-Perl/
# ['Sophos SAVI', \&ask_daemon, ['{}','savi-perl:'] ],
# ['Avira SAVAPI',
# \&ask_daemon, ["*", 'savapi:/var/tmp/.savapi3', 'product-id'],
# qr/^(200|210)/m, qr/^(310|420|319)/m,
# qr/^(?:310|420)[,\s]*(?:.* <<< )?(.+?)(?: ; |$)/m ],
# settings for the SAVAPI3.conf: ArchiveScan=1, HeurLevel=2, MailboxScan=1
### http://www.clamav.net/
['ClamAV-clamd',
\&ask_daemon, ["CONTSCAN {}\n", "/run/clamd.amavisd/clamd.sock"],
qr/\bOK$/m, qr/\bFOUND$/m,
qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ],
# NOTE: run clamd under the same user as amavisd - or run it under its own
# uid such as clamav, add user clamav to the amavis group, and then add
# AllowSupplementaryGroups to clamd.conf;
# NOTE: match socket name (LocalSocket) in clamav.conf to the socket name in
# this entry; when running chrooted one may prefer a socket under $MYHOME.
# ### http://www.clamav.net/ and CPAN (memory-hungry! clamd is preferred)
# # note that Mail::ClamAV requires perl to be build with threading!
# ['Mail::ClamAV', \&ask_daemon, ['{}','clamav-perl:'],
# [0], [1], qr/^INFECTED: (.+)/m],
# ### http://www.openantivirus.org/
# ['OpenAntiVirus ScannerDaemon (OAV)',
# \&ask_daemon, ["SCAN {}\n", '127.0.0.1:8127'],
# qr/^OK/m, qr/^FOUND: /m, qr/^FOUND: (.+)/m ],
# ### http://www.vanja.com/tools/trophie/
# ['Trophie',
# \&ask_daemon, ["{}/\n", 'trophie:/run/trophie'],
# qr/(?x)^ 0+ ( : | [\000\r\n]* $)/m, qr/(?x)^ 1 ( : | [\000\r\n]* $)/m,
# qr/(?x)^ [-+]? \d+ : (.*?) [\000\r\n]* $/m ],
# ### http://www.grisoft.com/
# ['AVG Anti-Virus',
# \&ask_daemon, ["SCAN {}\n", '127.0.0.1:55555'],
# qr/^200/m, qr/^403/m, qr/^403[- ].*: ([^\r\n]+)/m ],
# ### http://www.f-prot.com/
# ['F-Prot fpscand', # F-PROT Antivirus for BSD/Linux/Solaris, version 6
# \&ask_daemon,
# ["SCAN FILE {}/*\n", '127.0.0.1:10200'],
# qr/^(0|8|64) /m,
# qr/^([1235679]|1[01345]) |<[^>:]*(?i)(infected|suspicious|unwanted)/m,
# qr/(?i)<[^>:]*(?:infected|suspicious|unwanted)[^>:]*: ([^>]*)>/m ],
# ### http://www.f-prot.com/
# ['F-Prot f-protd', # old version
# \&ask_daemon,
# ["GET {}/*?-dumb%20-archive%20-packed HTTP/1.0\r\n\r\n",
# ['127.0.0.1:10200', '127.0.0.1:10201', '127.0.0.1:10202',
# '127.0.0.1:10203', '127.0.0.1:10204'] ],
# qr/(?i)<summary[^>]*>clean<\/summary>/m,
# qr/(?i)<summary[^>]*>infected<\/summary>/m,
# qr/(?i)<name>(.+)<\/name>/m ],
# ### http://www.sald.com/, http://www.dials.ru/english/, http://www.drweb.ru/
# ['DrWebD', \&ask_daemon, # DrWebD 4.31 or later
# [pack('N',1). # DRWEBD_SCAN_CMD
# pack('N',0x00280001). # DONT_CHANGEMAIL, IS_MAIL, RETURN_VIRUSES
# pack('N', # path length
# length("$TEMPBASE/amavis-yyyymmddTHHMMSS-xxxxx/parts/pxxx")).
# '{}/*'. # path
# pack('N',0). # content size
# pack('N',0),
# '/var/drweb/run/drwebd.sock',
# # '/var/amavis/run/drwebd.sock', # suitable for chroot
# # '/usr/local/drweb/run/drwebd.sock', # FreeBSD drweb ports default
# # '127.0.0.1:3000', # or over an inet socket
# ],
# qr/\A\x00[\x10\x11][\x00\x10]\x00/sm, # IS_CLEAN,EVAL_KEY; SKIPPED
# qr/\A\x00[\x00\x01][\x00\x10][\x20\x40\x80]/sm,# KNOWN_V,UNKNOWN_V,V._MODIF
# qr/\A.{12}(?:infected with )?([^\x00]+)\x00/sm,
# ],
# # NOTE: If using amavis-milter, change length to:
# # length("$TEMPBASE/amavis-milter-xxxxxxxxxxxxxx/parts/pxxx").
### http://www.kaspersky.com/ (kav4mailservers)
['KasperskyLab AVP - aveclient',
['/usr/local/kav/bin/aveclient','/usr/local/share/kav/bin/aveclient',
'/opt/kav/5.5/kav4mailservers/bin/aveclient','aveclient'],
'-p /run/aveserver -s {}/*',
[0,3,6,8], qr/\b(INFECTED|SUSPICION|SUSPICIOUS)\b/m,
qr/(?:INFECTED|WARNING|SUSPICION|SUSPICIOUS) (.+)/m,
],
# NOTE: one may prefer [0],[2,3,4,5], depending on how suspicious,
# currupted or protected archives are to be handled
### http://www.kaspersky.com/
['KasperskyLab AntiViral Toolkit Pro (AVP)', ['avp'],
'-* -P -B -Y -O- {}', [0,3,6,8], [2,4], # any use for -A -K ?
qr/infected: (.+)/m,
sub {chdir('/opt/AVP') or die "Can't chdir to AVP: $!"},
sub {chdir($TEMPBASE) or die "Can't chdir back to $TEMPBASE $!"},
],
### The kavdaemon and AVPDaemonClient have been removed from Kasperky
### products and replaced by aveserver and aveclient
['KasperskyLab AVPDaemonClient',
[ '/opt/AVP/kavdaemon', 'kavdaemon',
'/opt/AVP/AvpDaemonClient', 'AvpDaemonClient',
'/opt/AVP/AvpTeamDream', 'AvpTeamDream',
'/opt/AVP/avpdc', 'avpdc' ],
"-f=$TEMPBASE {}", [0,8], [3,4,5,6], qr/infected: ([^\r\n]+)/m ],
# change the startup-script in /etc/init.d/kavd to:
# DPARMS="-* -Y -dl -f=/var/amavis /var/amavis"
# (or perhaps: DPARMS="-I0 -Y -* /var/amavis" )
# adjusting /var/amavis above to match your $TEMPBASE.
# The '-f=/var/amavis' is needed if not running it as root, so it
# can find, read, and write its pid file, etc., see 'man kavdaemon'.
# defUnix.prf: there must be an entry "*/var/amavis" (or whatever
# directory $TEMPBASE specifies) in the 'Names=' section.
# cd /opt/AVP/DaemonClients; configure; cd Sample; make
# cp AvpDaemonClient /opt/AVP/
# su - vscan -c "${PREFIX}/kavdaemon ${DPARMS}"
### http://www.centralcommand.com/
['CentralCommand Vexira (new) vascan',
['vascan','/usr/lib/Vexira/vascan'],
"-a s --timeout=60 --temp=$TEMPBASE -y $QUARANTINEDIR ".
"--log=/var/log/vascan.log {}",
[0,3], [1,2,5],
qr/(?x)^\s* (?:virus|iworm|macro|mutant|sequence|trojan)\ found:\ ( [^\]\s']+ )\ \.\.\.\ /m ],
# Adjust the path of the binary and the virus database as needed.
# 'vascan' does not allow to have the temp directory to be the same as
# the quarantine directory, and the quarantine option can not be disabled.
# If $QUARANTINEDIR is not used, then another directory must be specified
# to appease 'vascan'. Move status 3 to the second list if password
# protected files are to be considered infected.
### http://www.avira.com/
### old Avira AntiVir 2.x (ex H+BEDV) or old CentralCommand Vexira Antivirus
['Avira AntiVir', ['antivir','vexira'],
'--allfiles -noboot -nombr -rs -s -z {}', [0], qr/ALERT:|VIRUS:/m,
qr/(?x)^\s* (?: ALERT: \s* (?: \[ | [^']* ' ) |
(?i) VIRUS:\ .*?\ virus\ '?) ( [^\]\s']+ )/m ],
# NOTE: if you only have a demo version, remove -z and add 214, as in:
# '--allfiles -noboot -nombr -rs -s {}', [0,214], qr/ALERT:|VIRUS:/,
### http://www.avira.com/
### Avira for UNIX 3.x
['Avira AntiVir', ['avscan'],
'-s --batch --alert-action=none {}', [0,4], qr/(?:ALERT|FUND):/m,
qr/(?:ALERT|FUND): (?:.* <<< )?(.+?)(?: ; |$)/m ],
### http://www.commandsoftware.com/
['Command AntiVirus for Linux', 'csav',
'-all -archive -packed {}', [50], [51,52,53],
qr/Infection: (.+)/m ],
### http://www.symantec.com/
['Symantec CarrierScan via Symantec CommandLineScanner',
'cscmdline', '-a scan -i 1 -v -s 127.0.0.1:7777 {}',
qr/^Files Infected:\s+0$/m, qr/^Infected\b/m,
qr/^(?:Info|Virus Name):\s+(.+)/m ],
### http://www.symantec.com/
['Symantec AntiVirus Scan Engine',
'savsecls', '-server 127.0.0.1:7777 -mode scanrepair -details -verbose {}',
[0], qr/^Infected\b/m,
qr/^(?:Info|Virus Name):\s+(.+)/m ],
# NOTE: check options and patterns to see which entry better applies
# ### http://www.f-secure.com/products/anti-virus/ version 5.52
# ['F-Secure Antivirus for Linux servers',
# ['/opt/f-secure/fsav/bin/fsav', 'fsav'],
# '--virus-action1=report --archive=yes --auto=yes '.
# '--dumb=yes --list=no --mime=yes {}', [0], [3,4,6,8],
# qr/(?:infection|Infected|Suspected|Riskware): (.+)/m ],
# # NOTE: internal archive handling may be switched off by '--archive=no'
# # to prevent fsav from exiting with status 9 on broken archives
### http://www.f-secure.com/ version 9.14
['F-Secure Linux Security',
['/opt/f-secure/fsav/bin/fsav', 'fsav'],
'--virus-action1=report --archive=yes --auto=yes '.
'--list=no --nomimeerr {}', [0], [3,4,6,8],
qr/(?:infection|Infected|Suspected|Riskware): (.+)/m ],
# NOTE: internal archive handling may be switched off by '--archive=no'
# to prevent fsav from exiting with status 9 on broken archives
# ### http://www.avast.com/
# ['avast! Antivirus daemon',
# \&ask_daemon, # greets with 220, terminate with QUIT
# ["SCAN {}\015\012QUIT\015\012", '/run/avast4/mailscanner.sock'],
# qr/\t\[\+\]/m, qr/\t\[L\]\t/m, qr/\t\[L\]\t[0-9]+\s+([^[ \t\015\012]+)/m ],
# ### http://www.avast.com/
# ['avast! Antivirus - Client/Server Version', 'avastlite',
# '-a /run/avast4/mailscanner.sock -n {}', [0], [1],
# qr/\t\[L\]\t([^[ \t\015\012]+)/m ],
['CAI InoculateIT', 'inocucmd', # retired product
'-sec -nex {}', [0], [100],
qr/was infected by virus (.+)/m ],
# see: http://www.flatmtn.com/computer/Linux-Antivirus_CAI.html
### http://www3.ca.com/Solutions/Product.asp?ID=156 (ex InoculateIT)
['CAI eTrust Antivirus', 'etrust-wrapper',
'-arc -nex -spm h {}', [0], [101],
qr/is infected by virus: (.+)/m ],
# NOTE: requires suid wrapper around inocmd32; consider flag: -mod reviewer
# see http://marc.theaimsgroup.com/?l=amavis-user&m=109229779912783
### http://mks.com.pl/english.html
['MkS_Vir for Linux (beta)', ['mks32','mks'],
'-s {}/*', [0], [1,2],
qr/--[ \t]*(.+)/m ],
### http://mks.com.pl/english.html
['MkS_Vir daemon', 'mksscan',
'-s -q {}', [0], [1..7],
qr/^... (\S+)/m ],
# ### http://www.nod32.com/, version v2.52 (old)
# ['ESET NOD32 for Linux Mail servers',
# ['/opt/eset/nod32/bin/nod32cli', 'nod32cli'],
# '--subdir --files -z --sfx --rtp --adware --unsafe --pattern --heur '.
# '-w -a --action-on-infected=accept --action-on-uncleanable=accept '.
# '--action-on-notscanned=accept {}',
# [0,3], [1,2], qr/virus="([^"]+)"/m ],
# ### http://www.eset.com/, version v2.7 (old)
# ['ESET NOD32 Linux Mail Server - command line interface',
# ['/usr/bin/nod32cli', '/opt/eset/nod32/bin/nod32cli', 'nod32cli'],
# '--subdir {}', [0,3], [1,2], qr/virus="([^"]+)"/m ],
# ### http://www.eset.com/, version 2.71.12
# ['ESET Software ESETS Command Line Interface',
# ['/usr/bin/esets_cli', 'esets_cli'],
# '--subdir {}', [0], [1,2,3], qr/virus="([^"]+)"/m ],
### http://www.eset.com/, version 3.0
['ESET Software ESETS Command Line Interface',
['/usr/bin/esets_cli', 'esets_cli'],
'--subdir {}', [0], [1,2,3],
qr/:\s*action="(?!accepted)[^"]*"\n.*:\s*virus="([^"]*)"/m ],
## http://www.nod32.com/, NOD32LFS version 2.5 and above
['ESET NOD32 for Linux File servers',
['/opt/eset/nod32/sbin/nod32','nod32'],
'--files -z --mail --sfx --rtp --adware --unsafe --pattern --heur '.
'-w -a --action=1 -b {}',
[0], [1,10], qr/^object=.*, virus="(.*?)",/m ],
# Experimental, based on posting from Rado Dibarbora (Dibo) on 2002-05-31
# ['ESET Software NOD32 Client/Server (NOD32SS)',
# \&ask_daemon2, # greets with 200, persistent, terminate with QUIT
# ["SCAN {}/*\r\n", '127.0.0.1:8448' ],
# qr/^200 File OK/m, qr/^201 /m, qr/^201 (.+)/m ],
### http://www.norman.com/products_nvc.shtml
['Norman Virus Control v5 / Linux', 'nvcc',
'-c -l:0 -s -u -temp:$TEMPBASE {}', [0,10,11], [1,2,14],
qr/(?i).* virus in .* -> \'(.+)\'/m ],
### http://www.pandasoftware.com/
['Panda CommandLineSecure 9 for Linux',
['/opt/pavcl/usr/bin/pavcl','pavcl'],
'-auto -aex -heu -cmp -nbr -nor -nos -eng -nob {}',
qr/Number of files infected[ .]*: 0+(?!\d)/m,
qr/Number of files infected[ .]*: 0*[1-9]/m,
qr/Found virus :\s*(\S+)/m ],
# NOTE: for efficiency, start the Panda in resident mode with 'pavcl -tsr'
# before starting amavisd - the bases are then loaded only once at startup.
# To reload bases in a signature update script:
# /opt/pavcl/usr/bin/pavcl -tsr -ulr; /opt/pavcl/usr/bin/pavcl -tsr
# Please review other options of pavcl, for example:
# -nomalw, -nojoke, -nodial, -nohackt, -nospyw, -nocookies
# ### http://www.pandasoftware.com/
# ['Panda Antivirus for Linux', ['pavcl'],
# '-TSR -aut -aex -heu -cmp -nbr -nor -nso -eng {}',
# [0], [0x10, 0x30, 0x50, 0x70, 0x90, 0xB0, 0xD0, 0xF0],
# qr/Found virus :\s*(\S+)/m ],
# GeCAD AV technology is acquired by Microsoft; RAV has been discontinued.
# Check your RAV license terms before fiddling with the following two lines!
# ['GeCAD RAV AntiVirus 8', 'ravav',
# '--all --archive --mail {}', [1], [2,3,4,5], qr/Infected: (.+)/m ],
# # NOTE: the command line switches changed with scan engine 8.5 !
# # (btw, assigning stdin to /dev/null causes RAV to fail)
### http://www.nai.com/
['NAI McAfee AntiVirus (uvscan)', 'uvscan',
'--secure -rv --mime --summary --noboot - {}', [0], [13],
qr/(?x) Found (?:
\ the\ (.+)\ (?:virus|trojan) |
\ (?:virus|trojan)\ or\ variant\ ([^ ]+) |
:\ (.+)\ NOT\ a\ virus)/m,
# sub {$ENV{LD_PRELOAD}='/lib/libc.so.6'},
# sub {delete $ENV{LD_PRELOAD}},
],
# NOTE1: with RH9: force the dynamic linker to look at /lib/libc.so.6 before
# anything else by setting environment variable LD_PRELOAD=/lib/libc.so.6
# and then clear it when finished to avoid confusing anything else.
# NOTE2: to treat encrypted files as viruses replace the [13] with:
# qr/^\s{5,}(Found|is password-protected|.*(virus|trojan))/
### http://www.virusbuster.hu/en/
['VirusBuster', ['vbuster', 'vbengcl'],
"{} -ss -i '*' -log=$MYHOME/vbuster.log", [0], [1],
qr/: '(.*)' - Virus/m ],
# VirusBuster Ltd. does not support the daemon version for the workstation
# engine (vbuster-eng-1.12-linux-i386-libc6.tgz) any longer. The names of
# binaries, some parameters AND return codes have changed (from 3 to 1).
# See also the new Vexira entry 'vascan' which is possibly related.
# ### http://www.virusbuster.hu/en/
# ['VirusBuster (Client + Daemon)', 'vbengd',
# '-f -log scandir {}', [0], [3],
# qr/Virus found = (.*);/m ],
# # HINT: for an infected file it always returns 3,
# # although the man-page tells a different story
### http://www.cyber.com/
['CyberSoft VFind', 'vfind',
'--vexit {}/*', [0], [23], qr/##==>>>> VIRUS ID: CVDL (.+)/m,
# sub {$ENV{VSTK_HOME}='/usr/lib/vstk'},
],
# ### http://www.avast.com/ (old)
# ['avast! Antivirus', ['/usr/bin/avastcmd','avastcmd'],
# '-a -i -n -t=A {}', [0], [1], qr/\binfected by:\s+([^ \t\n\[\]]+)/m ],
# ### http://www.avast.com/
# ['avast! Antivirus', '/bin/scan', '{}', [0], [1], qr/\t(.+)/m ],
### http://www.ikarus-software.com/
['Ikarus AntiVirus for Linux', 'ikarus',
'{}', [0], [40], qr/Signature (.+) found/m ],
### http://www.bitdefender.com/
['BitDefender', 'bdscan', # new version
'--action=ignore --no-list {}', qr/^Infected files\s*:\s*0+(?!\d)/m,
qr/^(?:Infected files|Identified viruses|Suspect files)\s*:\s*0*[1-9]/m,
qr/(?:suspected|infected)\s*:\s*(.*)(?:\033|$)/m ],
### http://www.bitdefender.com/
['BitDefender', 'bdc', # old version
'--arc --mail {}', qr/^Infected files *:0+(?!\d)/m,
qr/^(?:Infected files|Identified viruses|Suspect files) *:0*[1-9]/m,
qr/(?:suspected|infected): (.*)(?:\033|$)/m ],
# consider also: --all --nowarn --alev=15 --flev=15. The --all argument may
# not apply to your version of bdc, check documentation and see 'bdc --help'
### ArcaVir for Linux and Unix http://www.arcabit.pl/
['ArcaVir for Linux', ['arcacmd','arcacmd.static'],
'-v 1 -summary 0 -s {}', [0], [1,2],
qr/(?:VIR|WIR):[ \t]*(.+)/m ],
# ### a generic SMTP-client interface to a SMTP-based virus scanner
# ['av_smtp', \&ask_av_smtp,
# ['{}', 'smtp:[127.0.0.1]:5525', 'dummy@localhost'],
# qr/^2/, qr/^5/, qr/^\s*(.*?)\s*$/m ],
# ['File::Scan', sub {Amavis::AV::ask_av(sub{
# use File::Scan; my($fn)=@_;
# my($f)=File::Scan->new(max_txt_size=>0, max_bin_size=>0);
# my($vname) = $f->scan($fn);
# $f->error ? (2,"Error: ".$f->error)
# : ($vname ne '') ? (1,"$vname FOUND") : (0,"Clean")}, @_) },
# ["{}/*"], [0], [1], qr/^(.*) FOUND$/m ],
# ### fully-fledged checker for JPEG marker segments of invalid length
# ['check-jpeg',
# sub { use JpegTester (); Amavis::AV::ask_av(\&JpegTester::test_jpeg, @_) },
# ["{}/*"], undef, [1], qr/^(bad jpeg: .*)$/m ],
# # NOTE: place file JpegTester.pm somewhere where Perl can find it,
# # for example in /usr/local/lib/perl5/site_perl
);
@av_scanners_backup = (
### http://www.clamav.net/ - backs up clamd or Mail::ClamAV
['ClamAV-clamscan', 'clamscan',
"--stdout --no-summary -r --tempdir=$TEMPBASE {}",
[0], qr/:.*\sFOUND$/m, qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ],
# ### http://www.clamav.net/ - using remote clamd scanner as a backup
# ['ClamAV-clamdscan', 'clamdscan',
# "--stdout --no-summary --config-file=/etc/clamd-client.conf {}",
# [0], qr/:.*\sFOUND$/m, qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ],
# ['ClamAV-clamd-stream',
# \&ask_daemon, ["*", 'clamd:/run/clamav/clamd.sock'],
# qr/\bOK$/m, qr/\bFOUND$/m,
# qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ],
### http://www.f-prot.com/ - backs up F-Prot Daemon, V6
['F-PROT Antivirus for UNIX', ['fpscan'],
'--report --mount --adware {}', # consider: --applications -s 4 -u 3 -z 10
[0,8,64], [1,2,3, 4+1,4+2,4+3, 8+1,8+2,8+3, 12+1,12+2,12+3],
qr/^\[Found\s+[^\]]*\]\s+<([^ \t(>]*)/m ],
### http://www.f-prot.com/ - backs up F-Prot Daemon (old)
['FRISK F-Prot Antivirus', ['f-prot','f-prot.sh'],
'-dumb -archive -packed {}', [0,8], [3,6], # or: [0], [3,6,8],
qr/(?:Infection:|security risk named) (.+)|\s+contains\s+(.+)$/m ],
### http://www.trendmicro.com/ - backs up Trophie
['Trend Micro FileScanner', ['/etc/iscan/vscan','vscan'],
'-za -a {}', [0], qr/Found virus/m, qr/Found virus (.+) in/m ],
### http://www.sald.com/, http://drweb.imshop.de/ - backs up DrWebD
['drweb - DrWeb Antivirus', # security LHA hole in Dr.Web 4.33 and earlier
['/usr/local/drweb/drweb', '/opt/drweb/drweb', 'drweb'],
'-path={} -al -go -ot -cn -upn -ok-',
[0,32], [1,9,33], qr' infected (?:with|by)(?: virus)? (.*)$'m ],
### http://www.kaspersky.com/
['Kaspersky Antivirus v5.5',
['/opt/kaspersky/kav4fs/bin/kav4fs-kavscanner',
'/opt/kav/5.5/kav4unix/bin/kavscanner',
'/opt/kav/5.5/kav4mailservers/bin/kavscanner', 'kavscanner'],
'-i0 -xn -xp -mn -R -ePASBME {}/*', [0,10,15], [5,20,21,25],
qr/(?:INFECTED|WARNING|SUSPICION|SUSPICIOUS) (.*)/m,
# sub {chdir('/opt/kav/bin') or die "Can't chdir to kav: $!"},
# sub {chdir($TEMPBASE) or die "Can't chdir back to $TEMPBASE $!"},
],
### http://www.sophos.com/
['Sophos Anti Virus (savscan)', # formerly known as 'sweep'
['/opt/sophos-av/bin/savscan', 'savscan'], # 'sweep'
'-nb -f -all -rec -ss -sc -archive -cab -mime -oe -tnef '.
'--no-reset-atime {}',
[0,2], qr/Virus .*? found/m,
qr/^>>> Virus(?: fragment)? '?(.*?)'? found/m,
],
# other options to consider: -idedir=/usr/local/sav
# A name 'sweep' clashes with a name of an audio editor (Debian and FreeBSD).
# Make sure the correct 'sweep' is found in the path if using the old name.
# Always succeeds and considers mail clean.
# Potentially useful when all other scanners fail and it is desirable
# to let mail continue to flow with no virus checking (when uncommented).
# ['always-clean', sub {0}],
);
1; # insure a defined return value
Windows Outlookの設定
WindowsのOutlookから、当該メールサーバーへ接続した場合に、自己証明書を利用していることから以下の警告「証明書チェーンは処理されましたが、信頼プロバイダーが信頼していないルート証明書で強制終了しました。」が表示されます。このサーバーの使用を続けますか?「はい」でメールの送受信は可能ですが、少々煩わしいです。
これを回避するには、メールサーバー上で作成した認証局の証明書をWindowsにインストールすれば回避できます。ただしWindowsではPEM形式の証明書は読み込みができませんのでDER形式に変換する必要があります。
# cd /etc/pki/postfix # openssl x509 -inform PEM -in cacert.pem -outform DER -out cacert.der
上記で作成されたcacert.derをWindows側に移送し、ダブルクリックし、「証明書のインストール」ボタンを押下すると証明書インポートウィザードが起動しますので、「信頼されたルート証明機関」として保存しましょう。
これで煩わしい警告ポップアップはでなくなるはずです。
記事は以上!

![[Linuxウィルス対策]Sophos Antivirus for Linux のインストール方法](https://blog.kamata-net.com/media/celtispack/thumbnail/6d33cac4ec69b7bd15adf108e668e2df-full.png)
 TOSHIO-WEB
TOSHIO-WEB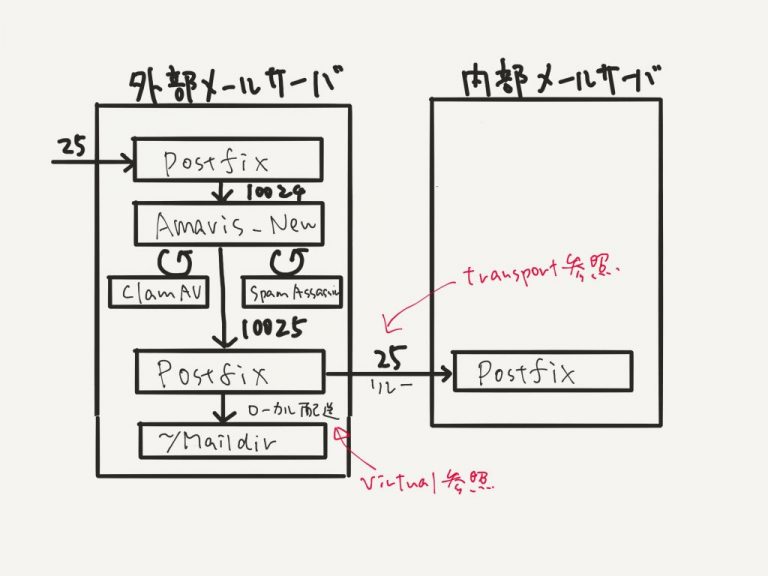
 Valimail
Valimail